Organizations use third-party service providers to reduce costs and benefit from the expertise that is not available within the organization. SOC 2 compliance was developed to regulate and ensure the safety of consumer data, while this cooperation blooms.
Third-party service providers are sometimes the outsourcing firms, software companies providing software as service solutions, or IT helpdesk support services at a minimum.
Critical data processed by these service providers, if mishandled, can lead to data breaches, compliance issues, and financial losses.
With more service companies moving their data storage to cloud infrastructures, organizations are even more concerned about data management processes. There are many elements to data management, including data security, privacy, availability, confidentiality, and data integrity.
Enterprise organizations and multinational corporations, in particular, are as worried about a vendor’s data management and security requirements as they are about the quality of the vendor’s product or service. In the absence of a globally accepted certification, these service providers find it difficult to close large contract negotiations with prospective clients unless they can convince the client of the necessity of data protection and secure information management.
And that’s where System and Organization Controls Certification (SOC) comes in.
“Achieving SOC 2 certification was a pivotal move for our clients. Before, we were buried in vendor assessments; now, we’re serious contenders for enterprise deals, with those spreadsheets becoming a non-issue.
Jacek Głodek
In this article we’ll cover:
- What is SOC 2 and how it’s different from SOC 1 and SOC 3
- What goes in a SOC 2 audit report
- Who is qualified to conduct SOC 2 audits
- Whi is SOC 2 for
- Benefits of SOC 2 compliance
- What you need to become compliant
Need help developing your software solution? At Iterators, we design, build, and maintain custom software and apps for startups and enterprise businesses.
Schedule a free consultation with Iterators. We’re happy to help you find the right solution.
What is SOC2?
System and Organization Controls (SOC) for service organizations was developed by the American Institute of Public Accountants (AICPA); it is a report on the internal controls on the services provided by a service organization that its clients need to assess and address the risks associated with an outsourced service.
SOC is a framework to evaluate whether controls and policies are operating effectively to protect its customers’ data safety and confidentiality.
It is an audited accreditation that assesses service providers’ data security requirements and information management controls when storing client information.
There are three types of SOC reports, SOC 1, SOC 2, and SOC 3. SOC 1 and SOC 2 reports are more commonly used than SOC 3.
SOC compliance is a minimum criterion for security-conscious enterprises when looking for a service provider.
As a foundation for data protection, it is based on five “Trust Services Criteria“: security, availability, consistency of processing, confidentiality, and privacy.
The AICPA’s Assurance Services Executive Committee (ASEC) defined the control criteria in the 2017 Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy.
SOC 1 vs. SOC 2
Let’s talk briefly about the differences between a SOC 1 and SOC 2 report. A SOC 1 audit reports on the systems and internal controls pertinent to the financial information of its clients. The most common use of SOC 1 report is by the statutory auditors of the service providers’ clients.
The control objectives for a SOC 1 audit include procedures for processing and securing customers’ information across both business and IT systems with an impact on its financial statement reports.
So how a SOC 2 is different from SOC 1 – a SOC 2 report primarily evaluates and reflects on a commercial organization’s internal controls and systems related to clients’ data security, availability, processing integrity, confidentiality, and privacy.
The control objectives of a SOC 2 audit can include any combination of the five trust principles. Some service companies may choose to be evaluated across all five trust principles, while others select one or more.
When deciding between both SOC reports, a service organization should consider the requirements of its key clients. SOC 1 certification will cover the controls around the financial data of its clients and help address the requirements of its clients’ auditor during annual audits. In comparison, a SOC 2 audit reports on internal controls related to clients’ data security, availability, processing integrity, confidentiality, and privacy.
Who Is Qualified to Conduct a SOC Audit?
Only an independent CPA (Certified Public Accountant) or accounting firm can conduct a SOC audit. The AICPA regulates SOC auditors and requires them to follow certain professional standards. Members of the AICPA must also submit to peer reviews to ensure that the audits they carried out are in compliance with recognized auditing standards.
Non-CPA individuals with pertinent information technology audit and security certifications can be employed by CPA firms to prepare SOC audits. However, a CPA must issue the official report.
What Does a SOC 2 Report Entail?
A SOC 2 report, issued by auditors, is shared by the service organization with its customers or prospective customers, or other stakeholders to show that sufficient controls are in place to protect the service they provide.
Because there is no exhaustive set of “thou shalt” requirements, SOC 2s diverge from several other data security standards and frameworks. The AICPA provides guidance on the general criteria that a service organization might use to demonstrate that it has controls in place to manage risks associated with the service it provides.
This might be aggravating for some first-time clients because there is no one-size-fits-all solution for addressing the relevant criteria. A professional auditor can advise the service organization to figure out what the service organization is already doing to meet the appropriate criteria and identify any gaps for remediation.
SOC 2 reports are unique to each organization, in contrast to the stringent criteria of GDPR compliance, PCI DSS compliance, and HIPAA compliance. Every company creates its own controls to ensure that one or more of the trust principles are followed per its business practices. These reports provide vital information about how network operators manage data provided to and collected from their consumers, business partners, regulators, vendors, suppliers, and others.
SOC 2 reports are divided into two categories. SOC 2 Type I reports describe a vendor’s systems and whether they can effectively meet applicable trust criteria. The productive capacity of these systems is described in SOC 2 Type II reports.
Organizations that complete the compliance procedure will receive a seven-part report confirming their controls to reduce security risks. The report contains the following:
- The Assertion part explains how the five TSCs and the security controls interact.
- The independent auditor’s report assesses the effectiveness of the controls in place.
- The system overview report explains how the service organization and its service providers work together.
- All components of business operations, including staff, security, and software procedures, are summarized in the infrastructure part.
- The relevant aspects of the controls part examine the effectiveness of communication protocols, the methodology used to conduct risk assessments, and the surveillance controls to track usage and security systems.
- The complementary user-entity controls part details the common platform with a service organization and the security procedures that protect the user environment.
- The test of controls part assesses controls effectiveness after testing and provides an assessment stating whether the controls were effective.
What Does a SOC 2 Audit Report Contain?
A SOC 2 report is intended to reassure service organizations’ clients, management, and user entities about the applicability and efficacy of security, scalability, processing consistency, anonymity, and privacy measures. The report is intended for existing or potential clients only.
SOC audits and reports are divided into two categories:
- Type 1 – The audits and reports are completed on a set date.
- Type 2 – The audit and report take place over a set time, usually at least six months.

Before 2014, cloud companies only had to comply with SOC 1 criteria. To limit risk and exposure to consumer data stored in the cloud, all organizations must comply with SOC 2 criteria.
So, what are the requirements for SOC 2?
The SOC 2 is classified as a technical audit, but it’s more than that: service organizations must design and execute strong information security policies and processes that cover the security, accessibility, processing, integrity, and confidentiality of consumer data, according to SOC 2. SOC 2 certifies that an organization’s information security procedures meet the specific requirements of today’s cloud systems. SOC 2 compliance is becoming a requirement for a wide range of enterprises as corporations increasingly use the cloud to store consumer data.
To put this into perspective, listed below are the four important areas of security practices for SOC 2 compliance.
What the SOC 2 Is Not
SOC 2 is not a checklist of policies, tools, or processes that must be followed. Rather, it identifies the criteria that must be met to maintain strong cyber security, allowing each firm to adopt the practices and processes that are most relevant to its goals and operations.
The following are the five Trust Services Criteria
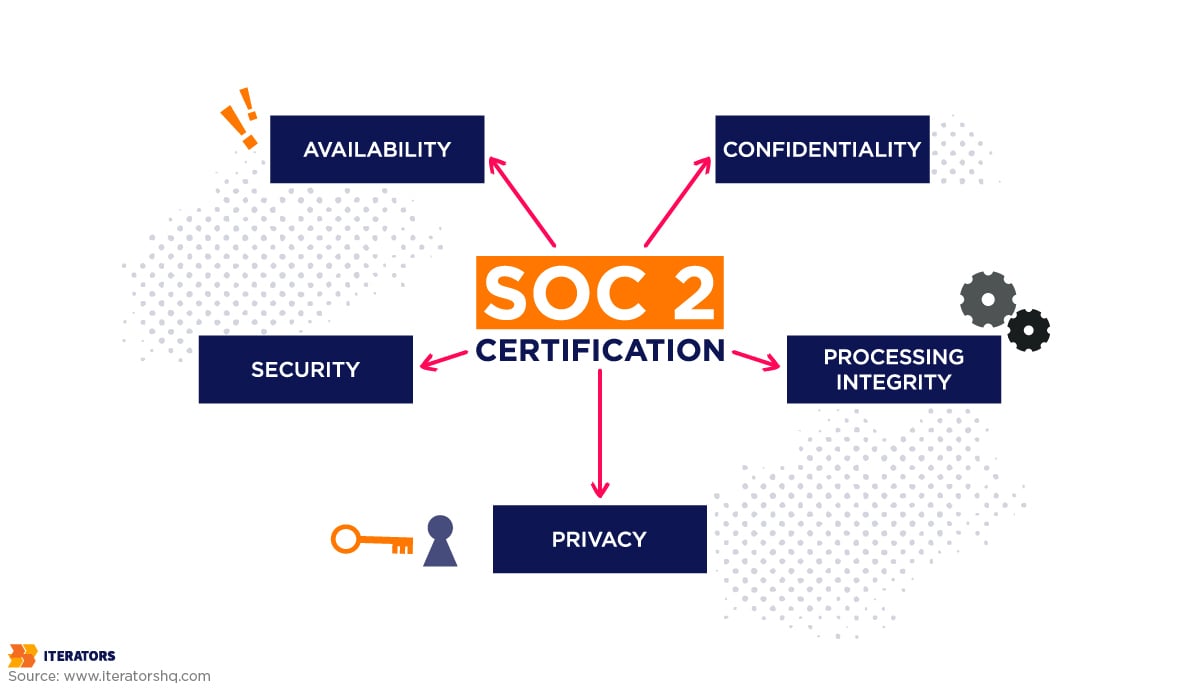
- Security: The term “security” refers to safeguarding data and systems against unauthorized access. This could be accomplished by implementing IT security infrastructures such as firewalls, two-factor authentication, and other safeguards to protect your data from illegal access.
- Availability: Availability refers to whether the hardware, technology, or information is up to date and has operational, monitoring, and servicing controls. This criterion also examines and minimizes potential external risks and whether or not your firm maintains minimum acceptable network performance standards.
- Processing Integrity: Processing integrity means that systems execute as intended—with no errors, delays, omissions, or unauthorized or inadvertent modification. This also means that data processing procedures are authorized, complete, and precise and work as they should.
- Confidentiality refers to a company’s capacity to safeguard data that should only be shared with a limited number of people or organizations. Client data intended only for corporate personnel use, secret business information, such as business strategies or intellectual property, and any other information mandated to be protected by law, legislation, contract, or agreement falls under this category.
Privacy: The privacy criteria is the measurement of the ability of an organization to protect personally identifiable information from unwanted access. This information is typically in the form of a person’s name, Social Security Number (SSN), address, and other identifiers like race, ethnicity, or health records.
Does SOC 2 apply to your business?
If your company is an emerging software company that hosts customer data or a service provider that handles and processes customer data, you should go for a SOC 2 certification. Generally, SOC 2 applies to any technical service provider, including organizations’ operation as software as a service (SaaS) – these organizations handle or store consumer data. To preserve the integrity of their data systems and safeguards, such firms’ third-party vendors, other partners, or support organizations should likewise be SOC 2 compliant.
While SOC 2 compliance isn’t required for SAAS and cloud providers, its importance in data security cannot be understated. The client company may request an assurance audit report from the service organization, especially if the service organization hands confidential or sensitive data.
A SOC 2 certification will go a long way in establishing trust with clients and stakeholders if your company delivers cloud services. For service organizations to collaborate with or offer services to tier-one companies, a SOC 2 audit is required to cover the full calendar year.
It’s worth noting that, from the perspective of selling a SaaS product, being SOC2 compliant is definitely important if you want to go after bigger clients. Fortune 500 companies require their software providers to have SOC2, and will also be more inclined to buy if you’re SOC2-compliant.
The Benefits of Becoming SOC 2 Compliant
In practice, there are many SOC 2 compliance benefits to the overall internal controls environment; some of the key benefits include:
- Your company is familiar with usual operations, routinely monitors for malicious or unidentified behavior, documents system configuration changes, and keeps track of user access levels.
- You have tools in place to detect risks and notify the appropriate parties, allowing them to assess the situation and take the needed steps to secure data and systems from unauthorized access or usage.
- You have all the information you need to assess the breadth of any security incidents, repair systems, or procedures as needed and restore data management integrity.
How to Maintain SOC 2 Compliance

- Keep an Eye on What’s Known (And the Unknown)
SOC 2 compliance means your organization has implemented a process and practices with the required levels of control. You’re specifically scanning for any anomalous system activity, permitted and unauthorized system configuration changes, and user access levels via a certain monitoring process.
That said, given how quickly things move in the cloud, you’ll need the capacity to keep an eye out not just for known harmful conduct but also for the unknown. This can be accomplished by establishing a baseline for everyday activities in your cloud environment, from which you can decide what constitutes aberrant behavior.
- Anomaly Warnings
When a security event occurs — and given the realities of today’s threat landscape, one is almost certain — you must demonstrate that adequate alerting mechanisms are in place so that if unauthorized access to client data occurs, you can respond quickly and take corrective measures.
Unfortunately, the difficulty with notifying is that false positives often result in a lot of noise. To counteract this, you’ll need a system that only sounds the alarms when activity strays from the standard set for your specific area.
SOC 2 mandates that businesses put up warnings for any acts that result in unauthorized:
- Data, settings, or configurations modification
- Activities involving file transfer
- Access to a restricted file system, account, or log in
In short, you must establish which actions inside your specific cloud environment and risk tolerance would be indicators of risks, so you can be warned as soon as they happen and take immediate action to prevent data loss or exposure.
- In-Depth Audit Trails
When it comes to responding to an attack, nothing is more crucial than understanding the fundamental reason. How would you know where to start fixing the problem if you don’t have that deep contextual understanding, especially if you’re responding to an active event?
The easiest way to collect the information you need to conduct your security operations is to use audit trails. These trails give you the critical cloud context to respond quickly and effectively, such as who, what, when, where, and how a security incident occurred.
Audit trails can provide you with valuable information about:
- Changes to, additions to, or deletions of essential system components
- Unapproved modifications to data and setups
- The impact location and the origin of the strike
- Actionable Forensics
Your consumers require assurance that you are not just watching for suspicious activity and receiving real-time notifications but also that you can respond to these indications before a system-wide crisis takes place and exposes or compromises sensitive customer data.
In addition to obsessing over reducing MTTD (mean time to detect), security firms should also concentrate on reducing MTTR (mean time to respond/remediate).
You need relevant data to make informed judgments since your decisions are only as great as the information you use to make them. This is accomplished through the use of host-based surveillance.
When you go directly to the source, you have access to the following information:
- The location where did the attack begun.
- The areas of the system it impacted and where it went.
- The impact’s characteristics.
- The action the company might take.
You can successfully detect threats, minimize their impact, and execute corrective actions to prevent similar incidents from reoccurring in the future using these forensics.
When Should You Become SOC 2 Compliant?
The correct answer: Right now—because your competitors are likely already SOC 2 certified.
From scrappy startups to sprawling conglomerates, every service organization that manages customer or client information should be consistent with this increasingly vital framework. SOC 2 certification, on the other hand, is not a simple task. It necessitates collaboration, forethought, coordination, audit findings, and more.
Meanwhile, your risk of data breaches is much higher than it should be. You might also be missing out on business opportunities.
Even if you already have SOC 1 certification, you still require a SOC 2 certification because it generates internal control reports based on five trust principles: data security, privacy, processing integrity, confidentially, and availability, whereas SOC 1 deals with financial reporting only.
It can take nine months or even a year to produce a SOC 2 report, particularly if you document your progress with spreadsheets.
How to Become SOC 2 Compliant in 7 Easy Steps
With so many moving pieces, regulations, and processes to align, achieving SOC 2 compliance can be a long and arduous task. A deliberate approach is the most effective. We recommend the following approach:
- Assign members to your SOC 2 team. The list above can assist you in deciding who should be a part of this crucial group.
- Determine your objectives. Do you need SOC 2 certification for a single product or service or your entire company?
- Determine the scope of your project. Which of the five Trust Services Categories in SOC 2 apply to your company? Which of the Trust Services Criteria from SOC 2 apply?
- Organize your supplies. Identify which controls apply to each Trust Services Criterion you selected in step 2, evaluate if they are successful, close any gaps, and compile the documents you’ll need as proof for each. Arrange evidence according to the five trust classifications: customer data protection, accessibility, confidentiality, processing integrity, and anonymity.
- Conduct a self-evaluation. The idea is to finish your assignment ahead of time. You may face audit reports and attestation rejection, which are more destructive than never seeking certification in the first place if you wait until the last minute to gather paperwork, construct an audit trail, and find and fill gaps.
- Keep an eye on yourself. Trying to set up security monitoring and alerts ahead of the SOC 2 auditor’s arrival will help you avoid falling out of compliance.
- A SOC 2 audit is a good idea. Only an impartial Certified Public Accountant is qualified to execute your SOC 2 audit, according to the AICPA. If necessary, your auditor may enlist the help of an independent, competent SOC 2 specialist.
Are you interested in management methodologies? Check out our article on operational excellence!
Conclusion
Compliance isn’t something you do once and then forget about. It’s a continuous activity that requires adhering to precise protocols that safeguard your clients. Threats are a continuous occurrence, especially in the cloud, and it’s your job to be a responsible steward of your client’s data.
SOC 2 compliance will enable your company to add layers of protection that will boost customer trust, minimize breaches, and improve your brand’s security status. However, SOC 2 is about establishing well-defined policies, procedures, and practices rather than simply checking all the compliance boxes using point solutions. So, sitting on your hands will serve you nothing.
Customers and end-users will be more confident in the security and functionality of your cloud infrastructure if you do it right.). SOC 2 Type 2 necessitates long-term, continual internal processes that will safeguard client information security and, as a result, the long-term success of your business.

