There’s always the chance that you’re vulnerable to attacks whenever someone from your organization browses the web, reads emails, or accesses mobile applications. Network security is a major challenge for businesses like yours. It stems from the growing significance of IT assets and the interconnection of information systems.
In the same vein, as your organization churns out data and information, processing, exchanging, and exploiting them, it’s necessary to consider the safety and security of the systems and networks on which this occurs. Vulnerability may cut across critical components and configurations, including applications, segmentations, servers, user access, workstations, and so forth.
Digital assets are a gateway into your organization’s systems. It’ll learn how to do this by increasing innovation in project and product management, improving efficiency, and minimizing the risk of disruption that could potentially impact customer, employee, and shareholder data.
Need help securing your digital assets? At Iterators we can help design, build, and maintain custom software solutions for both startups and enterprise businesses.
Schedule a free consultation with Iterators today. We’d be happy to help you find the right software solution to help your company.
Types of Things You Need to Secure Access to
A digital asset refers to anything that is stored in digital format, is uniquely identifiable, discoverable, and has or provides value for organizations.
Modern digital assets include documents, audio, videos, logos, slide presentations, spreadsheets, and websites. They’ve become more popular and valuable as organizational processes increasingly lean toward technology. Data, images, text, and visual content have long been categorized as digital assets with ownership rights.
Here are a few steps to secure your corporate digital assets:
- Identify your vulnerabilities by deploying cybersecurity threat hunting services. You can also update your anti-malware and antivirus systems, upgrade software and hardware, and enforce cybersecurity best practices across your organization.
- Perform regular audit trails to help you identify risky behavior. The frequency of audits may be annual, semiannual, quarterly, or monthly.
- Limit access to your digital assets so that only authorized personnel can open corporate files, photos, and customer databases.
- Back up your digital assets in accordance with fair-use regulations. There are enterprise data backup solutions that help you quickly recover original copies if some resources are maliciously or erroneously changed or deleted. This is helpful if the attacker has inserted malware in your systems and is demanding payment as you have a backup of the compromised digital assets in a secure place.
How to Secure Access to Your Domains and Web Services
Domain names and associated web services are essential to personal and professional concerns such as your organization. They’re important for online commerce and communication, making them critical assets that require the utmost attention in terms of security, according to the Internet Corporation for Assigned Names and Numbers (ICANN).
Here are ways to prevent unauthorized access to or loss of your domain name.
Choose a domain registrar with a sound verifiable reputation
Domain registrars manage your domain registration. While there are many of them, only a few have maintained a long standing reputation on the market.
Reputable registrars are accredited by ICANN. Popular accredited registrars in the US include Bluehost, Domain.com, GoDaddy, and Network Solutions. Begin by assessing reputation before considering factors such as cost and features.
Register your domain for the longest time possible
It’s advisable to make sure that you keep your domain registrations up to date. It ensures attackers won’t exploit the gap between registrations. Registering your domain for as long as possible means you’re less likely to forget to renew your registration.
Include a security contact for your company
A security contact improves domain security and can be done really quickly.
Your CTO (chief technical officer) or anyone operating in similar capacity is the ideal candidate for a security contact. But, you might be asking what happens when they leave your company or move to other roles. Well, that’s easy to deal with.
You can add, alter, or change security contacts at .gov registrar. All security contact modifications are publicly available in WHOIS – a public database of domain owners and their contact info.
A security contact streamlines threat reporting and receipt for your organization. It’s also advisable to add security contact information to your website to make it easier for anyone to reach your organization when issues arise.
Secure domain access by choosing a registrar offering protections
Always pay attention to domain access measures. Domain access is typically limited because most registrars require login credentials.
When choosing a registrar consider if they offer added protections like IP validation and two-factor authentication (2FA).
Consider registering look-alike domains
Look-alike domains appear similar to your primary domain, but may feature common misspellings. Examples include facebook.com vs. fcebook.com and google.com vs. goggle.com.
Remove all personal data from WHOIS
Personal data is an important tool in social engineering attacks. WHOIS is good for registering security contact information for your company. However, it’s best to remove details such as names, personal contact numbers, and email addresses. Use department information to prevent potential cases of identity theft.
Develop a vulnerability disclosure policy (VDP)
A vulnerability disclosure document outlines how your company receives and addresses vulnerability reports – a systematic review of security weaknesses in an information system. It’s recommended to involve your legal team when drafting your VDP, and you can use templates to know what to include.
Enable registry lock on your websites
Registry lock is a quick way to prevent unauthorized transfers or changes to your domain. It works great in preventing domain hijacking. The attacker won’t be able to access your registration data and gain administrative control over your domain name.

Services such as Verisign offer registry-level locking.
Prepare your domain for preloading
Preloading boosts your domain security when you submit your domain for inclusion in a browser’s HTTP Strict Transport Security (HSTS) preload list. Doing this enables browsers such as Google Chrome and Mozilla Firefox to automatically use HTTPS to connect to your website.
Use DMARC for email validation
Domain-based Message Authentication, Reporting and Conformance, or DMARC is a crucial piece in protecting your domain in email. It’s an email authentication policy/filter requiring one of SPF or DKIM “pass… authentication checks” and align with the domain in the sender’s address.
SPF is Sender Policy Framework, a policy that lets your business specify which email addresses can send email on behalf of your domain.
On the other hand, DKIM is concerned with cryptographic signing of individual email addresses. The acronym itself is DomainKeys Identified Mail. It enables you to authenticate the validity of an email message by cross-referencing the cryptographic signature in the domain header with the one the receiver calculates. Authentication only happens when the message is authenticated.
Safeguarding Code and Intellectual Property (IP)
The legal battle between tech giants Google and Oracle is well documented. The latter sued the search leader, alleging patent and copyright infringement. The courts had to decide whether Google included code from the Java technology codebase in its Android operating system.
Technological advancement has outpaced the US Copyright Act of 1976. It has led to problems in the software industry, with developers forced to depend on a confusing labyrinth of interpretations and assumptions without solid legal guarantees.
The question here is, how do you safeguard software code and intellectual property?
Intellectual property, or IP, refers to inventions, creations of the mind, images, symbols, commercial logos, or literary and artistic works. Businesses often tend to ignore IP rights as a key component of their business assets; you must do everything to avoid this often ugly scenario.
Your intellectual property is a priceless intangible asset that deserves protection. It improves your competitive advantage in the industry.
The US government provides tools and resources on intellectual property rights on Stopfakes.gov. This website offers business guides, country toolkits, scheduled training, and so forth.
Protecting IP and contractual agreements from unauthorized access or misuse

Intellectual property protection of your precious digital assets begins with the fundamental step of understanding copyrights. It involves works of authorship, including logos, books, software, and patents (for inventions). Other types of IP include designs, trademarks, and trade secrets.
In the United States, you begin safeguarding your intellectual property by first filing for protection. Depending on your state, the bar association can recommend experienced lawyers to guide your organization through the process.
In countries where your business has established a presence, you must be the first inventor to file for protection. It also applies where you’re considering doing business in the future. This filing is also necessary in countries with a thriving counterfeit market.
Intellectual property protections are naturally a part of the agreements when you do business in countries with a free trade agreement with the US. However, it’s advisable to file in each individual country to access those protections.
On the flip side, doing business in the European Union requires you only file for protection with the EU and not each nation.
It’s necessary to know that IP rights registered in the United States are territorial protections and do not necessarily hold water on foreign soil. Besides, most countries operate a “first to file” country for trademark registration and “first inventor to file” for patent registration. Therefore, registration is only granted to the first filer, no matter if they used it first in the market.
A key part of the conversation around copyrights and IP protections is when you implement team changes in your company. Former employees working for your competitors could become hard to deal with without the implementation of proper access restrictions when your talent moves to other companies or you lay them off.
Therefore, all IP should be transferred to the business once there’s a hint that an employee or contractor is leaving the organization.
Protecting Access to Payment Gateways and Marketing Panels
Payment gateways and marketing channels are critical systems in any enterprise. The former is cloud-based software connecting merchants with customers. When a customer wants to make a payment, it may be in-store at a POS (Point of Sale) or online via a webshop.
The payment gateway reads and transfers the payment information from the customer to the merchant’s bank account. It offers a smooth payment experience but presents fintech developers with yet another challenge: ensuring that it’s secure and adheres to industry standards.
However, it’s important to lay some groundwork for what goes on backstage when payment gateways make transactions possible.
- The customer commences the purchase, filling in their card details and clicking the Buy button. Alternatively, they’ll tap their card or mobile wallet onto a card reader.
- The payment gateway activates and checks the information for correctness by confirming from the issuing bank and ensuring there are enough funds.
- The payment gateway encrypts the transaction and forwards it to the relevant card schemes.
- Once approved by the card scheme, the payment gateway will send the information to the merchant’s bank.
- The payment gateway sends the encrypted information to the acquiring bank and moves the funds to finalize the transaction.
Payment gateways are a critical layer in the payments stack. They’re crucial in preventing and containing fraud attempts. Criminals stop at nothing in their quest to defraud individuals or businesses like yours. They may use phishing emails sent to your customers’ inboxes, “banks” calling to verify spending habits, or “alert” them to change their credit card PIN.
The more people transact business online, the more opportunities that fraudsters have to con them. This is a big issue for customers and merchants because the trust threshold is higher than ever. According to one report, online retailers face hundreds of thousands of fraudster attacks each month and were forecast to hit $1.5 billion in 2022 alone. And that’s just for Europe.
Thankfully, technology is evolving rapidly to detect financial fraud attempts in real-time and identify changes in behavior to pick out bad actors. Merchants need ongoing investment in these e-commerce fraud detection systems (especially those with artificial intelligence and machine learning capabilities) to improve the efficiency of detection and mitigation measures.
7 Ways to Boost Payment Gateway Security
Here are seven ways to dramatically improve the security of your payment gateway.
1. PCI DSS compliance

PCI DSS refers to the Payment Card Industry Data Security Standard, a set of compliance rules and security regulations implemented by the major card schemes.
You need PCI DSS compliance to process credit and debit card transactions. This ensures a secure environment for credit and debit transactions, preventing card theft and fraudulent activities from compromising card details.
Understanding PCI DSS standards will help you make the right choice when selecting a payment partner for your business.
2. Data encryption
Encrypting data is the main way that your payment gateway secures sensitive transaction data. When customers enter their card details at checkout, the payment gateway encrypts the data to only readable by those with a secret key. This greatly minimizes the probability of the data falling into the hands of someone inclined to misuse it.
3. Secure socket layer (SSL)
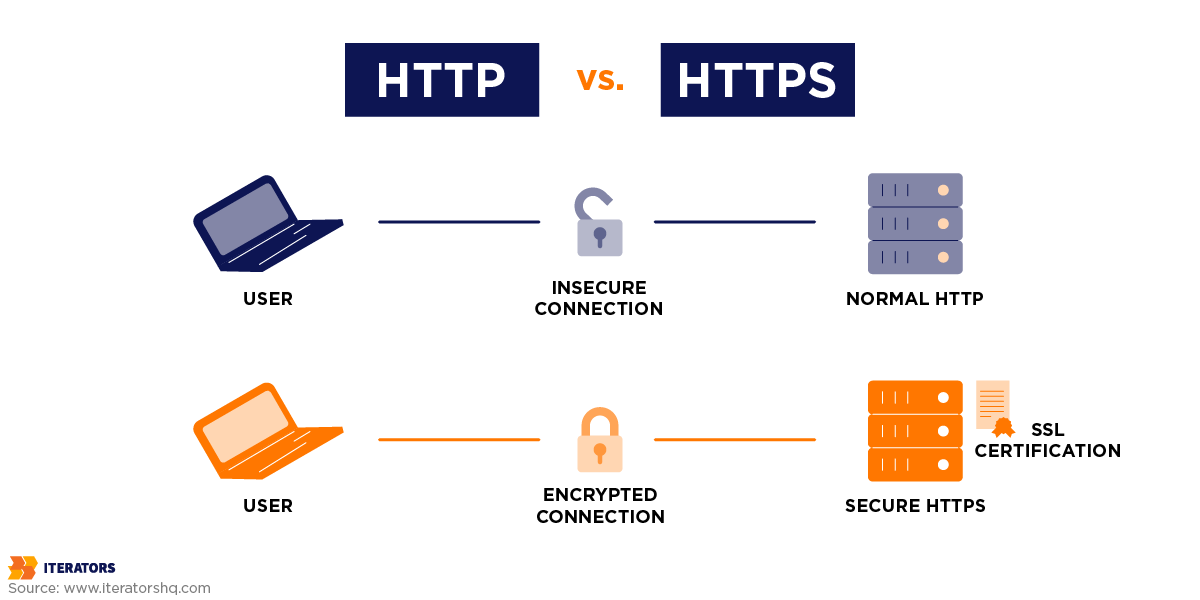
This security technology between the payments provider and the customer’s web client (such as a web browser) ensures that any data communicated via the SSL is encrypted.
SSL is a standard feature for web browsers, and if your website is directly processing a transaction, it should have SSL. However, SSL isn’t required if the website’s visitor is redirected to a secure checkout page on the domain of the payment gateway. The reason is that the payment gateway will provide the SSL link to the browser.
4. Secure electronic transaction (SET)

Secure electronic transaction or SET is an electronic protocol that encrypts the payment data of credit cards. It’s a joint initiative of Mastercard and VISA and conceals all personal details on the card, preventing criminals from accessing the information.
SET also ensures you won’t see customers’ personal data.
5. Tokenization
Tokenization converts the cardholder’s sensitive information into a security token. It involves encryption, hashing, and secret keys. Recall that card schemes only allow merchants to store card numbers unless they’re fully compliant with the PCI DSS framework; therefore, offering a payment gateway that uses tokenization is preferable.
Security improves with tokenization because sensitive information is only sent once over the internet when the token is created. It’s then usable for future payment requests.
6. 3d Secure 2.0
Also known as 3S2, 3DS 2.0, and EMV® 3- Secure, this authentication protocol from EMVCo resolves the issue of customer authentication in online payments.
Once a customer supplies their card details, they must fulfill the extra step of verifying their payment with their bank, usually through a password. This extra layer of protection prevents chargebacks and fraud while ensuring a friction-free experience across various marketing channels.
7. Adequate employee training

It’s crucial to have everyone on your payments processing team understand the latest industry regulations and compliances. Regular training and internal exams are necessary to ensure all employees know how to do the following effectively:
- handle payment data
- handle a data breach
- effectively inform customers
It’s important that the employee knowledge base be updated all the time to reflect current industry information and that everyone has the information at their fingertips. In summary, in order to keep your payment gateways secure, you could consider one of the following:
- Changing passwords regularly
- Rotating API keys often
- Using a password manager such as 1Password or Jumpcloud
- Managing roles and keeping centralized roles
- Maintaining a running log of all current accounts and deleting someone’s access once they leave the company
Preserving Access to Legacy Development Environments
A legacy system or development environment is any outdated computing system, software, or hardware your company still uses. Retaining these custom environments often makes economic sense because your organization has yet to recoup the hefty investment you made in acquiring them. New IT systems are usually expensive; businesses typically use them for a while before the value outweighs the costs.
The feature set of older systems is less robust than modern systems. Besides, they may still depend on outdated hardware or non-current security solutions. For on-premise solutions, they may even be unable to exploit the benefits of cloud technology or lack the open API that enables them to interface with other systems.
Not too long ago, the far-reaching effects of WannaCry and NotPetya exploited vulnerabilities in legacy operating systems (the SMB v1 protocol in this case). Known vulnerabilities are easy to deal with using patches and updates. But this will only benefit if your company makes sure to patch systems promptly. There are usually two issues that may hamper your approach to this:
- Are you aware of the presence of legacy systems in your organization?
- How easy is it to update these systems?
The legacy systems in your business environment may host applications critical to vital business processes. Here are a few principles to help you minimize the risk of keeping those legacy systems as part of your business.
1. Identify legacy systems
An effective cyber defense strategy is only possible with ample visibility and knowledge of your organization’s environment. Therefore, a discovery scan is an efficient tool to identify legacy systems.
A discovery scan also provides information about any system’s network architecture and vulnerabilities. Vulnerability scans should be a routine and ideally cover within and without the network.
2. Isolation followed by strict access control
Once you identify systems with no active support patches, immediately separate them from the pool of mission-critical organizational systems. It especially applies to endpoint networks. A single legacy system is a potential conduit to spread malware throughout a network.
Also, make sure that those systems aren’t explicitly accessible from the internet while ensuring that all communication with them is limited to minimal need. It’s possible if you place these systems in their own network segment behind a firewall or router.
3. Hardening
Relative to its purpose, hardening every system in your organization is recommended. It’s an important step for legacy systems. What is hardening, anyway? It refers to intentionally disabling any unnecessary service and implementing least privilege concepts to reduce general exposure.
Legacy operating systems, including Windows 2000, Windows ME, and Windows 2003, may be hardened by turning off the SMB protocol and other measures.
4. Constant monitoring
Security monitoring ensures that the system is in sync with the defined security baseline. It helps to detect suspicious activities early. Since many attacks typically happen alongside starting or stopping processes or altering permissions, monitoring should include security authentication and configuration events.
Legacy systems are urgent candidates for security monitoring, especially with respect to unwarranted access. These measures will help you to mitigate access risks if there’s no way to update a system. In the majority of cases, patch management and vigilant updating will protect your network from imminent access threats inside your legacy systems.
User Access, Credentials, and Contracts Management
User access management is one of the ways in which your company can improve data and information security in tandem with productivity. A system like that supports you in centralizing operations around creating and managing employee accounts while ensuring that IT administrators have improved security oversight.
User access management, or UAM, systems include technology tools for managing all the user roles across a company. They’re frameworks that control how your employees access different tools and systems.
Why You Need a User Access Management System
Here are some reasons why you need a UAM system.
- Improved security: You’d certainly like your IT departments to know who can access each system or account. It’ll help them to implement verification methods, identifying and mitigating any data breaches or threats by restricting access to current staff who have no need for certain information or former employees.
- Improved usability: With a UAM system, you can streamline access so that each person on your team can only access one central application and just the needed systems. It improves productivity and helps people to navigate to websites and programs they use quickly.
- Lower costs: UAM systems help to lower company IT overhead. It includes access management for separate systems and threat mitigation. Many of these cloud-based tools will also help to lower your infrastructure costs.
- Task automation: UAM tools also support integrating access information with other systems and tools. Your employees will spend more time on productive work than managing passwords, requesting access, and website/program navigation. Secure task automation is necessary in situations where staff are transferred across departments and work has to continue in seamless fashion.
- Reporting: Your UAM system will likely offer reporting features so you can see a list of users, the tools they can access, and authorizations all in one glance. It enables IT departments to comply with security regulations and adjust access levels as needed.
Effective User Access and Credential Management
These general requirements for user access management involve the following steps:
1. Ease of update
One key element of a user access management system is that it’s necessary to make it easy to update user accounts to enable teams to adjust settings quickly. It may require the following:
- setting up basic authorizations for certain accounts after creating them
- adding or removing access
- disabling accounts
One way to make account management easier is to allow users to request authorizations so that managers and a few others can approve or deny specific requests.
2. Security oversight
An effective UAM system can provide information about account profiles that may be at high risk. In the event of a data breach, the tool may reveal who changes the user directory or policies and report the changes made.
Security features may enable IT professionals to monitor and analyze these threats and implement changes that minimize their effects.
3. System Integration
Your company can manage data, document, and page access using UAM tools that integrate well with other systems, such as shared web portals. These compound systems enable you to view permissions directly on your websites instead of navigating to a separate access system.
UAM System integration supports user request permissions and IT departments to manage role profiles and authorizations.
4. Graphing features
Visuals can enable users, data owners, and administrators to view and understand user roles. This is where dashboards are a handy tool. For instance, you might need a pie chart to know who can access certain documents or systems.
Graphing features help identify if a user’s access complies with company policy and processes. Use graphics to view how each user or role performs certain functions, which can identify if you need to adjust permissions.
5. Compliance support
As UAM systems help ensure your company is in tandem with legal and company standards, compliance support, such as auditing tools and reporting, is critical. It can involve reviewing all user roles and individual activity to ensure compliance. For example, people may need to complete data security training before increasing their access, so reporting on this data can help identify whether all users are compliant.
Consider implementing strong password policies and credential management in the form of MFA or Multi-Factor Authentication.
Authorize and Access Your Systems and Platforms
There are a few necessary steps for effective user management that your IT department could use.
- Leverage restrictions: In order to minimize security threats and increase authority, it’s advisable to restrict authorizations to only the functions necessary for a person to do their job. It controls the number of unnecessary access that users could end up exploiting.
- Limit maximum privileges: Select high-level employees may prefer authorization to perform all functions. However, it’s best to allow it for only a few people. It can minimize inside threats having too much access or the quantity of information an external bad actor can have if they hack a superuser.
- Define role authorizations early: When installing a new UAM system, it’s recommended to determine roles and relative access levels to help with task automation. For instance, new employees might have a predetermined role to provide them with the functions necessary to do their jobs.
- Use password tools: Password managers and similar tools can promote security by ensuring employees only log in to their accounts using passwords from the IT department. It’ll limit password sharing and enhance security.
- Regularly review authorizations: While you may set authorization levels early, reviewing these roles often is necessary to ensure that each user has the appropriate access. Your IT department could request that managers review their roles to verify if each employee still needs the same access levels as when they began.
Third-Party Technologies and Repositories
Your company will inevitably use third-party technologies. These software technologies may be open-source or closed-source. The latter is mostly proprietary software and comes with a license that prohibits users from digging around the codebase and tweaking it in any manner. On the other hand, open-source software permits your in-house developers to play around with the code and customize it to suit your operations.
However, it’s best to assume that these applications from external sources come with significant risks because they do. Passing sensitive data through them such as customer personal information or customer account details poses an unmeasured level of risk, especially if they provide an essential component or service for your business. The operational risk involved could be of immense proportions.
Third-party risk management enables organizations to monitor and assess the risk from third parties to pinpoint where it supersedes the threshold set by your org. It will enable your teams to make risk-informed decisions, minimizing the risk originating from vendors to an acceptable level.
Major Challenges in Risk Management
Vendor risk management was once a time-consuming and error-prone procedure comprising manual processes that utilized emails, spreadsheets, and siloed vendor risk management tools.
The processes and tools needed to be improved. In addition, the number of third parties outpaced the capacity of teams and tools. These are the challenges you’ll likely face until you’re ready to implement modern comprehensive risk management solutions:
- Disconnecting: Like other companies, there’s a good chance you delay prioritizing third-party risks when requirements change or through the vendor lifecycle.
- Manual processes: There often needs to be higher efficiency in monitoring third parties, and it takes a long time to discover and mitigate issues.
- Lack of scalability: Using a barely scalable tool makes it harder to be in step with third-party risk management, thereby increasing risk.
- Siloes: A growing number of siloes makes accessing risk information across the organization more difficult.
Factors to Consider When Onboarding a Software Vendor
These are some important considerations for choosing a third-party software vendor. The answers will determine the level of risk they pose to your business:
- What type of data are they accessing? What type of access have you granted them?
- Does the vendor work with fourth parties that may present delivery challenges?
- Is the vendor in an unstable geographical location?
- Does the vendor provide a critical product or service? Can you line up alternatives?
- What’s the vendor’s security history, and what best practices have they established and executed? It includes basic software hygiene, patching SLAs (Service-Level Agreements), and a history of breaches.
- Does the vendor have any business continuity plans?
- Does the vendor comply with your organization’s identified regulations?
- What’s the vendor’s financial situation?

Steps to Core Asset and Third-party Risk Management
Here are a few essential steps in conducting core assets and even third-party risk management.
1. Onboarding
The experience of working with your in-house team or a third party entity comes with less friction when you’ve performed an initial risk assessment in your decision-making. Before formally engaging the all-clear.
2. Tier
It typically belongs in the initial risk assessment, done before onboarding, implementation.
In this scheme, Tier 1 includes the most critical vendors. In addition, some vendors may earn a place in a tier where regular assessment is not required.
External data from security ratings providers may help inform whether adjusting the tier level for a particular vendor is necessary.
3. Assessment
The higher a core digital asset or third party lies in the tier system, the more regular risk assessments should be. It depends on the area of risk posed by the vendor. Not all personnel or third parties need to answer questions about their security posture and financial viability.
The frequency of assessments depends on the tier, and the higher tiers are assessed more frequently.
4. Generate findings
Note that some responses must be completed or satisfactory after an assessment. Also, evaluate any objective external data collected around each digital asset or third party’s security and financial posture. Revert these issues or findings to the third party for response.
4. Remediate issues
There may come a time when an assessment swings back and forth within your team or with your third party, tasks are generated, issues are responded to, and evidence is provided as needed. Capture all communication for future reference, as some risks may be accepted.
5. Report risk
Report it to the appropriate parties once you identify, analyze, and remediate a risk. All parties deserve the level of visibility they prefer.
6. Monitor
Again, continuous assessment of all third parties and core assets is necessary, so you’ll need to monitor for changes in risk or performance. Frequent assessments or insights from external data sources, such as updated cybersecurity ratings, are helpful.
Changes should automatically lead to an issue, tier change, or assessment. The goal is for all third parties to fulfill expectations at an acceptable risk level continuously.
7. Retire
Your company needs a formal process to retire third parties and even core digital infrastructure and ensure all information not in permanent storage undergoes deletion.
The ultimate solution to eliminating third-party risk is to consider maintaining developer teams to build your mission-critical operations software. You ultimately have more control over what it does, how it does it, and how it utilizes any dependencies.
The Takeaway
Your organization needs software to compete well in the modern business climate. But, it also needs adequate preparation to deal with modern threats. It’s why you need comprehensive systems to protect your custom environment from unauthorized access. This is important in making sure that your customers enjoy uninterrupted access to your services.
We can help you build robust digital platforms that secure your digital assets and eliminate less secure communication mechanisms of legacy systems.

