You just acquired a hot new startup, but peeking under the hood, the tech stack looks like it belongs to the caveman days. Modernization is necessary, but a complete tech overhaul sounds like a recipe for disaster. This article is everything you need to take over any tech project with confidence.
We’ll equip you with three key strategies to revamp your system, assess its health, and navigate the inevitable challenges that come with any tech takeover. Get ready to transform that tech mess into a springboard for explosive growth.
Your Guide to Taking Over Like a Boss
If you’ve inherited a tech project, it can feel like a double-edged sword. You’ve got an established product with a user base, but the codebase may present major problems. Don’t sweat it! This section equips you with actionable knowledge to take over your project like a boss, transform that tech mess into a well-oiled machine, and get things running smoothly.
The Three Paths to Takeover
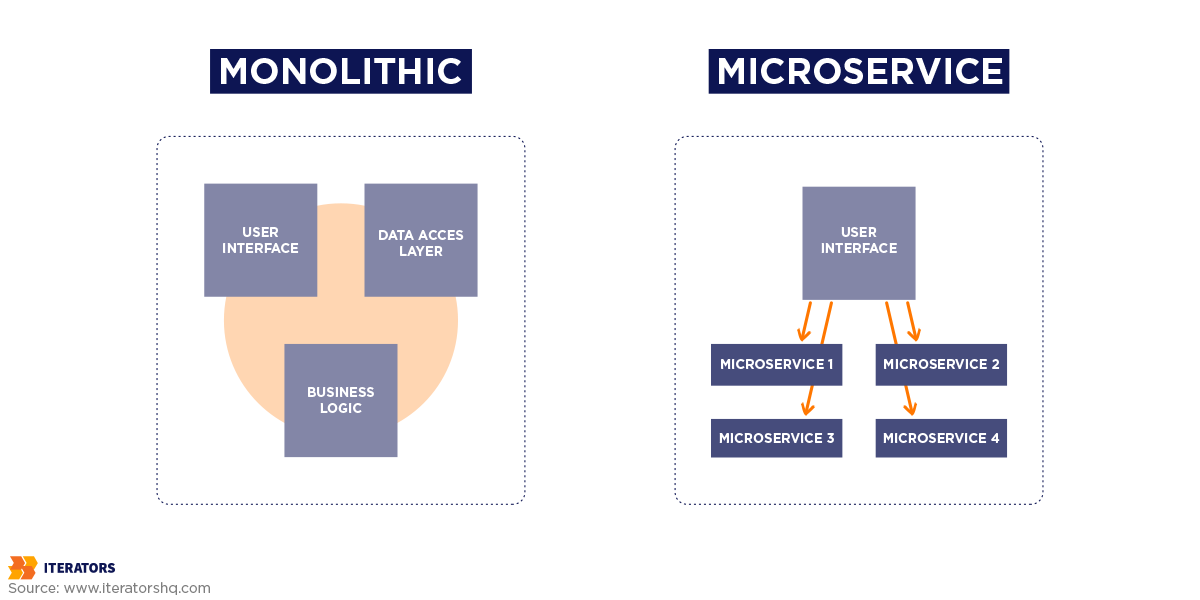
Inheriting a tech project can be both thrilling and daunting. It holds the potential for innovation, but the underlying code could be a bit like a vintage car – charming, but with a tendency to sputter. To ensure a smooth ride forward, you need to make a crucial “takeover” decision: rewrite, maintain the legacy system, or adopt a microservices architecture. Here’s a breakdown of each path, complete with real-world examples to help you choose the best fit.
1. Complete Rebuild (Rewrite)
Imagine ripping out the old engine and building a brand new one from scratch. This approach offers a clean slate, allowing you to integrate the latest features, robust security updates, and a modern codebase.
Advantages:
- Fresh Start: Perfect for projects with a severely outdated codebase, critical security vulnerabilities, or a complete shift in project vision. A rebuild lets you leverage the latest technologies and development practices.
- Enhanced User Experience: Modernize the interface and user experience to match current expectations.
- Improved Scalability: Build a system that can grow and adapt to future needs.
- Improved Business Knowledge: Do critical things more efficiently, avoiding previous mistakes, and positioning the team to deliver better products moving forward.
Disadvantages:
- Costly and Time-consuming: Requires significant developer resources and may cause disruptions to existing users during the rebuild phase.
- Potential Data Migration Issues: Moving existing data to a new system requires careful planning to avoid data loss or corruption.
Example
A social media platform built on a legacy system might struggle to keep pace with user demands and security threats. A complete rebuild allows them to integrate features like real-time messaging and enhanced privacy controls.
2. Maintaining the Legacy System
Think of this as keeping the old engine running smoothly with regular maintenance and tune-ups. You’ll continue to use the existing infrastructure while making improvements and optimizations.
Advantages:
- Faster and Less Risky: This approach minimizes disruption to users and can be implemented more quickly than a complete rewrite.
- Proven Functionality: Leverage the existing system’s stability and proven track record.
- Lower Cost: Requires less development effort compared to a rewrite.
Disadvantages:
- Limited Scalability: Legacy systems often struggle to handle significant increases in users or data volume.
- Integration Challenges: Integrating with modern technologies can be difficult.
- Talent Acquisition Challenges: Finding developers familiar with older programming languages, old or less compatible frameworks,adequate knowledge of the takeover, and possible technical debt, can be challenging.
Example
A bank’s core banking system, built on a reliable but aging platform, might benefit from ongoing maintenance and modernization to improve efficiency without disrupting critical financial transactions.
3. Microservices Architecture
Imagine transforming your car into a network of efficient, interchangeable modules, each with a specific function. These “microservices” communicate with each other to deliver the overall functionality of the project. This approach provides greater flexibility and scalability, allowing for faster development cycles and easier maintenance.
Advantages:
- Modular Design: Individual microservices can be developed, deployed, and scaled independently.
- Increased Agility: Faster development cycles and easier implementation of new features.
- Improved Maintainability: Easier to troubleshoot and fix issues within smaller services.
- Gradual Modernization with Legacy Integration: A microservices architecture can also be a powerful tool for gradually modernizing a legacy system. Here’s how it works:
- Wrap the Legacy System: Encapsulate the legacy system as a microservice within the new architecture. This exposes its functionality through a well-defined API.
- Stranglehold Pattern: Slowly develop new microservices that handle specific functionalities currently performed by the legacy system. The new microservices can interact with the legacy system through the API.
- Retirement Plan: As new microservices become available, gradually decommission functionality within the legacy system. This allows for a smooth transition to a fully modernized system built on microservices.
Disadvantages:
- Complexity: Managing and coordinating multiple services can be complex and requires skilled developers.
- Increased Development Effort: Designing and implementing a microservices architecture requires upfront investment.
- Potential Debugging Challenges: Issues can arise due to interactions between services.
Example
An e-commerce platform with a monolithic architecture might struggle to add new features and improve performance. By adopting microservices, they can build independent modules for product management, checkout, and user accounts, enabling faster development and easier scaling. This approach allows them to leverage the existing system while building a modern, scalable platform piece by piece.
Choosing the Right Path
The best approach depends on the specific needs of your project. Consider factors like the age of the codebase, scalability requirements, budget constraints, and available resources. By understanding the advantages and disadvantages of each path, you can confidently take over your tech project and steer it towards success.
A Glimpse into the Future
A successful tech takeover isn’t just about fixing the present; it’s about paving the way for a bright future. Here are some key benefits you can unlock:
- Enhanced Agility and Development Speed: Streamlined systems and modern architectures enable faster development cycles and easier implementation of new features.
- Improved Scalability and Performance: Modernized infrastructure can handle increased user loads and data volumes with greater efficiency.
- Reduced Maintenance Costs: Cleaner codebases and well-defined microservices can significantly reduce the time and resources needed for ongoing maintenance.
- Increased User Satisfaction: A smooth and reliable user experience translates to happier users and improved customer retention.
- Future-Proofing Your Project: A well-executed takeover strategy ensures your project is built on a foundation that can adapt and evolve alongside technological advancements.
Need help taking over a projects? The Iterators team can help design, build, and maintain custom software solutions for both startups and enterprise businesses.
Schedule a free consultation with Iterators today. We’d be happy to help you find the right software solution to help your company.
Assessing Your Tech Project’s Health
Before diving headfirst into a tech overhaul, it’s crucial to understand the current state of your project. Just like a doctor wouldn’t prescribe medicine without a diagnosis, taking the time to assess your tech project’s health is essential. This evaluation will reveal its strengths, weaknesses, and potential roadblocks, ultimately guiding you towards the most effective “take over” strategy.
Taking Your Tech Project’s Temperature
Here’s how to conduct a thorough checkup of your project:
- Codebase Review: Analyze the codebase for its age, complexity, and maintainability. Look for signs of outdated technologies, spaghetti code (difficult to understand and modify), and a lack of documentation.
- Functionality Assessment: Evaluate the current features and functionalities of the project. Are they meeting user needs? Are there critical features missing? How well does it perform under load?
- Scalability Analysis: Can the project handle future growth in users or data volume? Is the architecture flexible enough to accommodate new features?
- Security Audit: Assess the project’s security posture. Are there known vulnerabilities? Are there strong authentication and authorization mechanisms in place?
- Team Expertise: Evaluate the skills and experience of the development team. Do they have the necessary knowledge to maintain or rewrite the existing codebase?
- User Feedback: Gather feedback from users about their experience with the project. What are their pain points? What features would they like to see added?
Potential Roadblocks to Identify
By analyzing these factors, you can identify potential roadblocks that could impact your project’s future. Here are some common ones to watch out for:
- Technical Debt: A large amount of accumulated technical debt (code that needs to be refactored) can slow down development and increase maintenance costs.
- Integration Challenges: Difficulty integrating with new technologies or external systems can hinder progress.
- Talent Shortages: A lack of developers with the necessary skills to work on the project can delay development.
- Budgetary Constraints: Limited resources can make it difficult to implement major changes.
The best approach depends on the specific needs of your project. Consider the factors identified during your thorough assessment and weigh them against the advantages and disadvantages of each path (Rewrite, Legacy, Microservices) outlined earlier. By taking the time to diagnose your project’s health, you can confidently take over your tech project and steer it towards success.
Knowing Your Project’s Strengths and Weaknesses
Just like a mechanic wouldn’t rely on a hunch to diagnose a car, a successful tech takeover hinges on a thorough assessment. This toolbox equips you with three key methods to gauge your project’s health:
- Code Reviews: Imagine peering under the hood of your project. Code reviews involve diving deep into the codebase to identify outdated technologies, potential security vulnerabilities, and code quality issues. This analysis helps you understand the project’s foundation and potential areas for improvement.
- Performance Testing: Put your project to the test! Performance testing involves evaluating the project’s speed, scalability, and overall responsiveness under load. This is like taking your project for a high-performance test drive, revealing any bottlenecks or limitations that might hinder future growth.
- User Feedback Analysis: The voice of the user is invaluable! User feedback analysis involves listening to your user base to identify pain points, areas for improvement, and desired functionalities. By understanding how users interact with the project, you can identify opportunities to streamline the experience and ensure your “take over” strategy aligns with user needs.
Real-world Example of Successful Tech Takeover Assessment
Inheriting a monolithic codebase can be a major hurdle for tech companies. Slack, the popular communication platform, faced this challenge in its early days. Their initial codebase, while functional, struggled to keep pace with the platform’s rapid growth and user demands.
Recognizing the need for change, Slack conducted a thorough assessment of their tech infrastructure. This involved code reviews that identified limitations of the monolithic architecture, performance testing that revealed scalability bottlenecks, and user feedback analysis highlighting feature limitations.
Based on this assessment, Slack made the strategic decision to migrate towards a microservices architecture. This involved breaking down the platform’s functionality into smaller, independent services. Each microservice could be developed, deployed, and scaled independently, leading to greater agility and flexibility.
The success of Slack’s migration to microservices is well documented by Justin Patterson in his blog post, “Building Microservices at Slack.” The move enabled them to significantly improve scalability, allowing them to handle a much larger user base and integrate new features with greater ease. This case study highlights the importance of a well-defined assessment process in guiding successful tech takeovers.
When a Complete Rewrite Makes Sense

The assessment is complete, and the verdict is in: your tech project needs a major overhaul. But is a complete rewrite the right course of action, or are there other options? Here, we look into the world of codebase rewrites, exploring when a fresh start can be the most effective take over strategy for your project.
Code Red or Code Rewrite? When to Start from Scratch
After a less-than-satisfactory assessment, your tech project might be facing a full-blown “code red” situation where a tangled mess of code written in a language no one remembers, cripples performance that leaves users frustrated, or causes critical security vulnerabilities that make you sweat bullets.
While a complete rewrite might seem like the nuclear option, it can be the most effective take-over strategy in specific scenarios. Here’s when a rewrite might be your best bet:
- Legacy Codebase on Life Support: If your project is built on a foundation of incredibly outdated technologies like Cobol or Fortran, rewriting with modern tools and frameworks can offer a lifeline. Imagine trying to maintain a fleet of cars that run on leaded gasoline – a complete overhaul with modern, fuel-efficient engines can deliver significant performance improvements, enhanced security features, and easier maintenance for developers.
- Security Nightmares with No Easy Fix: If your project suffers from critical security vulnerabilities that can’t be easily patched with updates or workarounds, a rewrite might be the most responsible course of action. Think of it like a building with major structural flaws discovered during an earthquake – patching the cracks might not be enough; a complete rebuild might be necessary to ensure user safety and regain trust.
- Ground-Up Revolution with a New Vision: Sometimes, a complete rewrite is justified if your project’s vision has undergone a radical shift. If the core functionalities and architecture no longer align with your goals, a fresh start can be the most efficient way to achieve your new vision. Imagine wanting to transform a bicycle into a spaceship; a complete rebuild from the ground up using jet engines and advanced navigation systems might be your only option to reach the stars.
However, a rewrite is a significant undertaking, so proceed with caution. The next section will delve into the key considerations for navigating a codebase rewrite effectively, ensuring a smooth liftoff and a successful landing for your project.
Strategies for Prioritizing Functionalities in Legacy Code
A complete rewrite can feel like a fresh start for your project – a chance to shed the baggage of the old codebase and build a new foundation for the future. But with limited resources, not all functionalities can be included right away. This section equips you with strategies to prioritize functionalities during a rewrite, ensuring a lean and efficient core for your project’s new dawn.
Here are some key considerations for feature prioritization:
- Core Functionality First: Identify the Must-Have features that deliver the absolute value proposition of your project to your users. These are the non-negotiables that form the essential building blocks of your rewritten project. Imagine rebuilding a house – the foundation, walls, and roof are essential before adding features like a porch or a fancy kitchen.
- Business Impact vs. Development Effort: Analyze the impact of each feature on your business goals. Will a specific feature significantly increase user engagement, drive sales, or improve customer satisfaction? Weigh this impact against the development effort required for each feature. Focus on high-impact features that are relatively easy to implement in the initial phase of the rewrite. For example, a feature that allows users to easily search within the project might have a high impact on usability but require less development time compared to a complex recommendation engine.
- Phased Rollout with User Feedback: Consider a phased rollout strategy, releasing core functionalities first and iteratively adding more complex features based on user feedback and evolving business needs. This allows you to launch a valuable product quickly and gather valuable user insights to inform future development. Imagine launching a basic version of your food delivery app that allows users to browse menus and place orders. Based on user feedback, you can then prioritize features like real-time order tracking or integrated payment options in subsequent updates.
Minimizing User Disruption During the Rewrite
A complete rewrite can create a powerful engine for growth, but launching a half-built project can leave users feeling grounded. Would you like to learn new strategies to minimize user disruption during the rewrite, ensuring a smooth takeoff for your project’s next iteration?
Here are some key considerations for a user-friendly transition:
- Transparency is Key: Communication is your copilot. Keep your users informed throughout the rewrite process. Regularly communicate timelines, anticipated changes (both improvements and temporary limitations), and alternative solutions if functionalities are temporarily unavailable. Open communication builds trust, minimizes frustration, and allows users to mentally prepare for the new version.
- Phased Rollout with Feature Parity: Gradual Upgrades, Not Cliff Dives. Consider a phased rollout strategy, prioritizing core functionalities that users rely on most heavily. This allows users to continue utilizing the project with minimal disruption while ensuring feature parity with the original version before complete switchover. For example, if your e-commerce platform is undergoing a rewrite, prioritize features like product browsing and shopping cart functionality in the initial phase. Later phases can introduce new features like personalized recommendations or a more streamlined checkout process.
- Maintain an Optional Legacy Mode: A Safety Net for Apprehensive Flyers. For critical projects or situations where user comfort is paramount, offering a temporary “legacy mode” with the original functionalities can provide a safety net. This allows users who are hesitant to adopt the new interface to continue using the familiar version. However, this option should be clearly time-bound and phased out as users become comfortable with the rewritten version. Additionally, consider offering guided tours or tutorials for the new interface to ease user adoption.
These strategies can help you minimize user disruption and ensure a smooth transition to your project’s evolved form. After all, a happy and engaged user base is the jet fuel that propels your take over to success.
Software experts know that rewriting legacy code is a more significant undertaking than anyone may imagine. It’s important to carefully weigh the benefits versus the time and resource investment that it may require. For some projects, therefore, might be a more strategic approach.
Considering a complete rewrite? Ensure a smooth lift-off by engaging with the right team to help you to prioritize features during a codebase migration.
Living with a Legacy – Working with Existing Systems
A complete rewrite might sound appealing, but sometimes, the best course of action is to work with what you have. This section delves into the world of legacy systems, exploring strategies to keep your project running smoothly even with a less-than-ideal codebase.
Legacy Systems: Friend or Foe?
Inheriting a tech project can feel like receiving a vintage car – a classic with undeniable charm, but riddled with quirks and potential for breakdowns. While a shiny new model might be tempting, legacy systems, like those dependable vintage cars, can often offer surprising value. This section explores strategies to make the most of your existing tech inheritance, transforming it from a potential foe into a valuable ally on your path to project success.
Why Legacy Systems Deserve Another Look
Before diving headfirst into a complete overhaul, consider the advantages of leveraging your existing system:
- Proven Functionality: Legacy systems have often stood the test of time, reliably performing core functionalities for years. This established foundation can be a strong base upon which to build future improvements.
- Case Study: A bank might leverage its legacy core banking system, known for its stability and reliability in handling financial transactions, as the foundation for a new online banking platform. The bank can build a modern user interface and integrate with new features like mobile deposits and P2P payments, all while relying on the secure and proven backend functionality of the legacy system.
- Institutional Knowledge: Existing developers and users likely possess a deep understanding of the system’s intricacies. This knowledge can be invaluable for troubleshooting issues, maintaining the system, and ensuring a smooth transition during any future upgrades.
- Case Study: An insurance company with a legacy policy management system might decide to keep the core system due to the deep understanding of its data structures and business logic held by senior developers. This knowledge can be leveraged to develop integrations with new customer portals and fraud detection systems, reducing risk and development time.
- Lower Initial Costs: Compared to a complete rewrite, working with a legacy system can be significantly more cost-effective. This frees up resources that can be invested in strategic improvements and new feature development.
- Case Study: A state library’s legacy system was clunky, but a rewrite was too expensive. They chose to leverage the existing system’s core functionality and developed APIs to integrate with a modern, cloud-based library management system. Phased data migration minimized disruption. Lower initial costs, faster implementation, improved user experience, and increased staff efficiency.
Strategies for Success
Here are some key strategies to maximize the value of your legacy system:
- Leverage Existing Functionalities: Don’t reinvent the wheel! Identify and utilize the core functionalities that your legacy system performs well. This allows you to focus development efforts on enhancing existing features or building new functionalities on top of the existing foundation.
An e-commerce platform with a legacy order processing system can leverage that system’s strengths in order fulfillment and inventory management. The development team can focus on building a modern user interface for product browsing and shopping carts, improving the customer experience without rewriting the core functionality. - Implement Smart Integrations: Modern APIs and integration tools can bridge the gap between your legacy system and newer technologies. This allows you to integrate features from cloud-based services, mobile applications, or other modern tools, extending the capabilities of your project without rewriting the entire codebase.
A manufacturing company with a legacy production management system can integrate with a cloud-based business intelligence (BI) tool using APIs. This allows them to leverage the legacy system for shop floor control while using the BI tool for real-time data analysis and generating insightful reports, improving decision-making without modifying the core production system. - Prioritize Strategic Upgrades: Not all parts of a legacy system need immediate replacement. Focus on identifying performance bottlenecks, critical security vulnerabilities, or areas where functionality can be significantly improved. Invest in targeted upgrades to these areas for the most impactful results.
A manufacturing company with a legacy production management system can integrate with a cloud-based business intelligence (BI) tool using APIs. This allows them to leverage the legacy system for shop floor control while using the BI tool for real-time data analysis and generating insightful reports, improving decision-making without modifying the core production system. - Embrace Modern Development Practices: Even with a legacy codebase, modern development practices like code reviews, unit testing, and continuous integration can significantly improve code quality, maintainability, and developer efficiency.
A hospital with a legacy patient record system might identify a need to upgrade the user interface to improve usability for doctors and nurses. They can also prioritize a security upgrade to address potential vulnerabilities in data encryption. Upgrading these specific areas can significantly improve the system without replacing the entire infrastructure.
Remember also that legacy systems can evolve. By implementing these strategies and adopting a growth mindset, you can transform your inherited project from a clunky relic into a valuable asset, propelling your project forward and ensuring its continued success.
However, there are limitations to consider. If your legacy system suffers from severe performance issues, crippling security vulnerabilities, or an architecture that is fundamentally incompatible with future needs, a complete rewrite might be unavoidable. The next section will provide you with a framework to make this crucial decision.
How to Know When to Modernize or Integrate
After checking out the benefits of working with your existing system, it becomes urgent to consider a more substantial change. This provides a framework to decide between modernization and integration strategies, ensuring you choose the most effective path for your legacy system’s future.
When Modernization Makes Sense
- The Core Needs a Rebuild: If the codebase is outdated, riddled with security vulnerabilities, or fundamentally incompatible with modern development practices, a more extensive approach is likely necessary. Modernization through a rewrite or refactoring can rebuild the core functionalities using modern tools and frameworks (like microservices architectures), addressing these critical issues and creating a more secure, maintainable foundation for future growth.
- Scalability is a Major Hurdle: If your legacy system struggles to handle increasing user loads or data volumes, modernization can address these limitations. Modernization efforts can involve migrating the system to a cloud-based architecture or implementing more scalable database solutions. This ensures smooth future growth and avoids performance bottlenecks that could hinder your project’s success.
When Integration Might Be the Answer
- The Core Functionalities are Strong: If your legacy system performs core tasks like data processing or user authentication well, integration with modern tools and technologies can extend its functionality without a complete overhaul. Modern APIs and integration platforms allow you to seamlessly connect your legacy system with cloud-based services, mobile applications, or other modern tools. This injects new capabilities into your project while leveraging the existing strengths of your legacy system. Microservices can also be a great fit here – you can wrap the legacy system functionality in a microservice and integrate it with new, modern microservices for a piece-by-piece modernization approach.
- Time and Resources are Limited: Integration can be a faster and more cost-effective solution compared to a full-blown modernization project. This is especially true if the core functionalities of your legacy system are solid. Integration allows you to leverage existing functionalities while focusing development efforts on building new features or functionalities on top of the existing foundation, utilizing microservices for modular development and deployment.
Carefully considering these factors enables you to choose the most appropriate strategy to breathe new life into your legacy system. Whether you choose modernization or integration, the ultimate goal is to transform your inherited project into a valuable asset, propelling it forward and ensuring its continued success in the ever-evolving world of technology.
Data Security

Legacy systems might hold your project’s crown jewels – its vital user data, financial records, or intellectual property. Transitioning away from these systems requires meticulous planning to ensure data integrity and security. Even a minor data breach during migration can have devastating consequences. Here’s why data security deserves top priority:
- Maintaining Data Integrity: Any errors or inconsistencies during data transfer can corrupt valuable information. Rigorous data validation processes and clear data mapping procedures are essential to ensure your data arrives at its new destination accurately and completely.
- Preventing Security Breaches: Legacy systems might have vulnerabilities that weren’t previously a major concern. During migration, implement robust encryption measures to safeguard data in transit and at rest. Additionally, follow strict access control protocols to minimize the risk of unauthorized access.
Prioritizing data security ensures a smooth transition, protecting your project’s most valuable assets. Data breaches can erode user trust and damage your reputation. A proactive approach to data security safeguards your information and paves the way for a successful legacy system migration.
Success Story
The BBC, a titan in the world of broadcasting, faced a challenge – integrating its vast audio archives, containing decades of historical recordings, with its new streaming platform, BBC Sounds.
A complete rewrite of the archive system, while tempting, would have been a monumental task. Instead, the BBC took a smarter approach, showcasing the power of effectively leveraging legacy systems within a modern tech stack.
Here’s how the BBC achieved this success:
- Leveraging Legacy Strengths: BBC recognized that their legacy archive system excelled in audio processing and metadata management, crucial functionalities for their audio content. A complete rewrite wouldn’t necessarily improve upon these core strengths.
- Building a Modern API Layer: Instead of a full overhaul, the BBC engineers built a modern API (Application Programming Interface) layer on top of the existing archive system. This API acted as a translator, enabling seamless communication and data exchange between the legacy system and the new BBC Sounds platform.
- Modern Platform, Rich Audio History: By leveraging the API, BBC Sounds could access and present the vast audio library within its modern interface. This allowed BBC audiences to enjoy the BBC’s rich audio history alongside contemporary content, all within a single, user-friendly platform.
The BBC Sounds case study demonstrates that legacy systems don’t have to be a burden. By carefully evaluating functionalities and implementing creative integration strategies, you can bridge the gap between the old and the new, creating a harmonious blend of established strengths and modern capabilities.
Did you know? A whopping 70 percent of enterprise systems are considered legacy systems, highlighting the enduring presence of these established technologies within modern businesses.
Balancing Time and Resources

Legacy systems can be complex puzzles – a mix of potential and limitations. This section equips you with a framework for making informed decisions based on your specific project needs and resource constraints. Whether modernization, integration, or even co-existence with your legacy system is the best path forward, this section will guide you in choosing the most effective and resource-conscious strategy for your project’s success.
The Cost Equation
Legacy system transitions are financial crossroads. This section helps you navigate the cost equation by comparing the financial implications of each takeover approach:
| Option | Pros | Cons |
| Complete Rewrite | – Clean slate with modern technology; – Potentially reduced long-term maintenance; – Improved performance; | – Most expensive option; – High development time; – Resource allocation for project management, testing, and data migration; – Data migration costs; |
| Modernization through Microservices | – Less costly than rewrite; – Improved maintainability and efficiency (refactoring); – Enhanced scalability and security (migration); | Can still be a significant investment |
| Integration | – Most cost-effective; – Minimized development costs (APIs); – Faster turnaround time; – Reduced development effort; | – Ongoing maintenance of both systems; – Potential limitations in addressing core functionality issues; |
The most expensive option isn’t always the best. Carefully consider the long-term value proposition of each approach. A complete rewrite might seem costly upfront, but the benefits of a modern, efficient system could outweigh the initial investment. On the other hand, integration might be a faster and more cost-effective solution if your legacy system’s core functionalities remain strong.
Ultimately, the best path forward depends on a careful analysis of your project’s specific needs and budget constraints. The next section will provide a framework to help you make this crucial decision.
Team Dynamics
| Option | Required Skill Set |
| Complete Rewrite | – Expertise in modern technologies and frameworks; – Experience in building complex systems; – Data migration expertise; |
| Modernization through Microservices | – Legacy system knowledge; – Modern development practices; – Knowledge of target architectures (where applicable); |
| Integration | – API development and integration skills; – Understanding of legacy system capabilities; – Knowledge of modern tools to be integrated; |
Assessing your team’s strengths and weaknesses, you can identify any skill gaps that might need to be addressed through training or potential external hires. Remember, a well-equipped and motivated team is the driving force behind a successful legacy system takeover.
Estimating Timelines
Legacy system transitions are marathons, not sprints. This section provides a general idea of the timelines associated with each takeover path, helping you manage expectations and resource allocation effectively:
| Option | Timeline | Influencing Factors |
| Complete Rewrite | Month to years | – System complexity (larger, slower); – Team size and skillset (smaller/inexperienced, slower); – Data migration complexity (more data, slower); |
| Modernization through Microservices | Several months | Modernization Approach: – Refactoring (faster); – Migration to microservices/new architecture (slower due to learning curve); |
| Integration | Weeks to months | – Number of integrations (more integrations, slower); – Complexity of integrations (complex data handling, slower); |
The actual timeline for your project will depend on your specific circumstances. It’s crucial to involve your team in the planning process to get a more accurate time frame based on their expertise and the project’s unique requirements. By understanding the time commitment involved with each approach, you can make informed decisions, set realistic expectations for a successful takeover, and ensure a smooth transition for your project.
Making the Most of Your Time and Budget
Inheriting a tech project can strain your resources. Here’s a framework to navigate the decision between rewrite, legacy maintenance, or microservices while keeping time and budget in check:
- Define Success Metrics: Clearly outline your goals for the project. Are you prioritizing immediate user experience improvements, long-term scalability, or addressing security concerns?
- Timeboxing and Prioritization: Estimate the time and resources required for each path (rewrite, legacy, microservices). Consider a phased approach where you can address critical needs quickly and follow up with long-term improvements.
- Team Expertise and Availability: Evaluate your team’s skills and capacity. A rewrite might require external expertise, while leveraging a legacy system might be more manageable with your existing team.
- Total Cost of Ownership (TCO) Analysis: Factor in not just initial development costs, but also maintenance, scalability, and future upgrades when evaluating each approach.
By following these steps, you can make an informed decision that optimizes your time and resources, ensuring a successful future for your tech project.
Long-Term Vision
Legacy system takeovers are not one-time events. This section emphasizes the importance of aligning your chosen takeover strategy with your project’s long-term vision.
Consider:
- Scalability: Will your chosen approach support future growth and increased user demands?
- Maintainability: Is the resulting system built for future updates and easy integration with new technologies?
- Agility: How quickly can the system adapt to changing business needs and market trends?
A future-oriented approach ensures your legacy system takeover lays a solid foundation for your project’s long-term success.
Real-world example
Retail giant ABC faced a dilemma – their legacy inventory management system, while functional, lacked the real-time data capabilities needed for their new omnichannel strategy. A complete rewrite was tempting, but time constraints and resource limitations were major concerns. The solution? A strategic integration. ABC’s development team built APIs to connect their legacy system with a modern cloud-based inventory management platform. This approach leveraged the existing strengths of their legacy system while injecting the real-time functionalities needed for their omnichannel vision. The result? A successful and time-efficient takeover that propels ABC into the future of retail.
Mitigating Risks and Contingency Planning

Even the most meticulously planned legacy system takeover can encounter unexpected roadblocks. This section equips you with strategies to mitigate risks and create contingency plans to ensure a smooth and successful transition.
- Complete Rewrite:
- Scope Creep: New feature requests during development can balloon project timelines and budgets.
- Data Migration Issues: Errors or inconsistencies during data transfer can corrupt valuable information.
- Unforeseen Technical Challenges: The development process might uncover unforeseen technical complexities in the new system.
- Modernization:
- Limited Gains: Refactoring might not yield significant improvements if the core system architecture remains fundamentally flawed.
- Integration Challenges: Integrating modernized components with existing systems can introduce compatibility issues.
- Regression Bugs: Changes to the legacy codebase might introduce unintended bugs that require additional troubleshooting.
- Integration:
- API Limitations: Third-party APIs might not offer all the functionalities needed for a seamless integration.
- Security Vulnerabilities: Integration points can introduce new security risks if not properly secured.
- Increased System Complexity: Managing multiple interconnected systems can increase overall complexity and maintenance needs.
By proactively identifying potential risks, you can develop mitigation strategies and contingency plans to address them. The next section will guide you through this crucial process.
Building a Plan B (and C)
The best legacy system takeover plans are those that anticipate the unexpected. This section emphasizes the importance of developing contingency plans to address potential challenges that might arise during any of the takeover approaches:
- Clearly Define Risks and Triggers: Identify the most likely risks associated with your chosen path and establish clear trigger points. These triggers are specific events or situations that indicate a potential problem and signal the need to activate your contingency plan.
- Develop Alternative Solutions: For each identified risk, brainstorm and document alternative solutions. Think creatively about how you can adapt your approach or mitigate the impact of the issue.
- Prioritize and Assign Roles: Not all risks are created equal. Prioritize your contingency plans based on the likelihood and severity of each potential problem. Additionally, assign clear roles and responsibilities for implementing each contingency plan.
- Communication is Key: Ensure all stakeholders, from development teams to project managers, are aware of the contingency plans. Regular communication and transparent discussions about potential challenges foster trust and facilitate a smoother transition.
By developing robust contingency plans, you can navigate unexpected challenges with greater agility and ensure your legacy system takeover stays on track for success. Remember, a little planning goes a long way in mitigating risks and ensuring a successful and resilient project future.
Establishing Clear Communication Protocols
A successful legacy system takeover hinges on clear and consistent communication. This section highlights the importance of establishing communication protocols to manage stakeholders throughout the process:
- Regular Updates: Keep all stakeholders, from executives to end-users, informed of progress, potential roadblocks, and key milestones.
- Tailored Communication: Cater your communication style and level of detail to each stakeholder group. Technical updates for developers might differ from high-level summaries for executives.
- Open Channels: Establish clear channels for feedback and questions. Encourage open communication to address concerns and ensure everyone feels invested in the takeover’s success.
By following these strategies, you can foster a collaborative environment and navigate the takeover process with informed and engaged stakeholders.
Exit Strategy

Every successful journey needs a clear destination. This section emphasizes the importance of defining clear criteria for determining the success of your legacy system takeover initiative:
- Align Success with Project Goals:
- Start with “Why?”: Revisit the initial goals that prompted the legacy system takeover. Were you aiming to improve user experience, enhance scalability, or address security vulnerabilities?
- Metrics for Each Goal: Define measurable metrics for each project goal. This could involve user surveys for experience, performance benchmarks for speed and scalability, or security audit reports for improved posture.
- Specific and Measurable Criteria:
- Functional Requirements: Outline a clear list of functionalities the new system or integrated solution must deliver. This could involve specific features, integrations, or data migration accuracy.
- Performance Benchmarks: Set measurable performance targets. This might involve faster loading times, reduced response delays, or improved handling of increased user loads.
- User Satisfaction: Develop a user satisfaction survey or conduct usability testing to gauge user experience with the new system or integrated functionalities.
- Budget and Timeline Tracking: Monitor project progress against the allocated budget and established timeline. Track any deviations and implement corrective actions if necessary.
Examples
- E-commerce Platform Migration: Success criteria might include a 20% reduction in page load times, a 15% increase in successful checkout rates as measured by user behavior analytics, and a 90% user satisfaction rating based on post-launch surveys.
- Legacy Library System Integration: The project might be deemed successful if it achieves seamless integration with a new online library catalog, reduces data entry time for librarians by 30%, and maintains a 99.9% data accuracy rate.
By establishing clear, measurable success criteria upfront, you can objectively evaluate the effectiveness of your chosen takeover strategy and ensure a smooth transition for your legacy system. This data-driven approach allows you to celebrate your achievements and identify areas for further improvement, guaranteeing a triumphant landing for your project.
Lessons Learned
Legacy system takeovers, while complex, offer valuable lessons. Here are some key takeaways from successful projects:
- Planning is Paramount: Meticulous planning that considers risks, resources, and long-term goals paves the way for a smooth transition.
- Case Study: Migrating a Banking System: A bank meticulously planned their core banking system migration to a cloud-based solution. This involved detailed impact assessments, resource allocation planning, and phased data migration strategies. The planning phase also included extensive user training to ensure a smooth transition for employees and customers. This meticulous planning minimized downtime and ensured a successful migration.
- Embrace Agility: Be prepared to adapt your approach as unexpected challenges arise. Contingency plans and clear communication are crucial.
- Case Study: Insurance Policy Management Revamp: An insurance company encountered unforeseen data integrity issues during their legacy policy management system modernization. The agile team quickly adapted their approach, implementing additional data cleansing steps and revising their testing procedures. This flexibility ensured data accuracy in the new system and prevented delays.
- People Make the Difference: A skilled and motivated team equipped with the right tools and knowledge is essential for success.
- Case Study: Retail Supply Chain Integration: A retail company embarking on a legacy supply chain system integration assembled a cross-functional team. The team comprised developers with expertise in both the legacy system and the new integration platform, as well as business analysts who understood the logistics workflows. This blend of skills ensured a successful integration that optimized inventory management and order fulfillment.
Final Thoughts
Legacy systems can be transformed, not just replaced. This article equips you to choose the right approach (rewrite, modernize, or integrate) based on your project’s needs and resources. Plan for success by considering your team’s skills, timelines, and long-term vision. Anticipate challenges, communicate clearly, and define success metrics. Learn from successful takeovers: meticulous planning, adaptability, and a skilled team are key. Take control and transform your legacy system into a future-proof asset.
Ready to conquer your legacy system? Our tech takeover specialists at Iterators are available to offer valuable consultation to help you get off on a sound footing. Let’s chart your path to success together!
