Protecting digital assets and private data is highly important whether you’re running a startup or expanding a company. Web authentication is your first line of defense in guarding against unauthorized access and data theft. Without it your systems and data are vulnerable to attacks by malicious actors. Research has found that 30 percent of organizations have experienced a security breach due to weak authentication.
While password-based authentication is still common, recent technologies such as MFA, biometric, and token-based solutions provide increased security from modern threats. It’s important to know about these processes and procedures to protect your business from data breaches.
This article covers the most common web authentication methods, popular protocols, and what vulnerabilities you should look for. By the end, you’ll know which website authentication method is best suited for your needs, and how to implement it effectively.
What is Web Authentication
Web authentication is the process of confirming a user’s identity before allowing them to use an online resource, system, or service. It is an essential security feature that ensures only authorized users can access sensitive data, software, or platforms. This can be accomplished with usernames, passwords, or more sophisticated technologies like tokens, biometrics, and certificates.
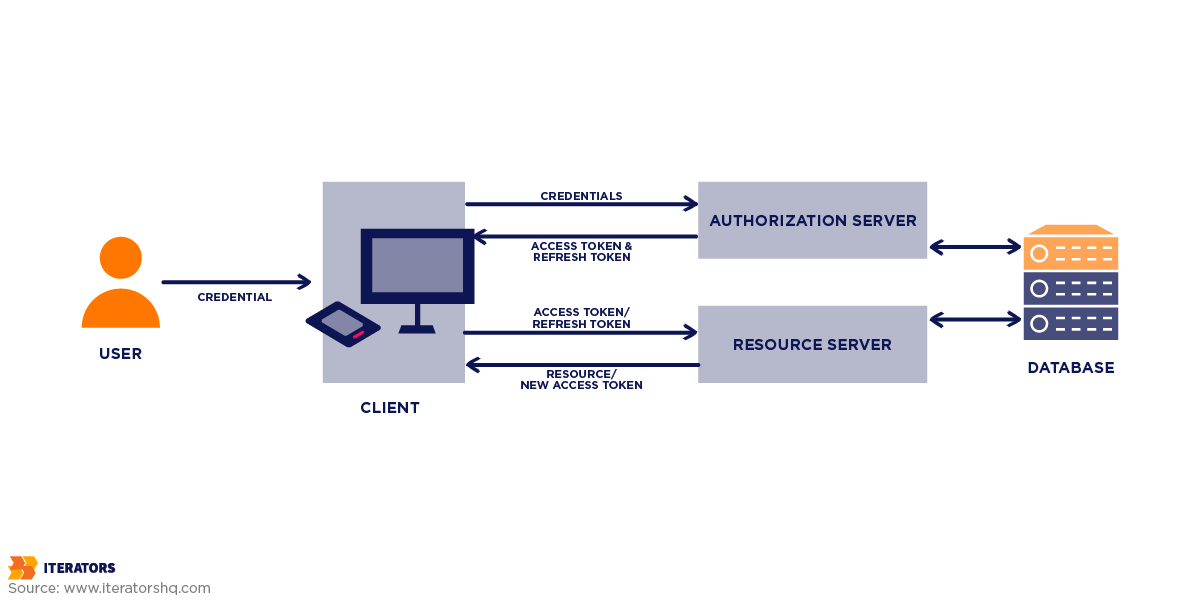
Web authentication is, essentially, a verification process between a user and a system. When a user logs in, their login information is sent to the system for validation. It generally goes like this:
- Step 1. Credential Input: The user gives their login credentials (username, password)
- Step 2. Transmission: These credentials are sent through encryption (e.g., HTTPS)
- Step 3. Verification: The server checks credentials against its database. If they are compatible, it gets access.
- Step 4. Session Management: When the user is verified, the server creates a session token to identify the user while they interact with the platform.
Implementing robust authentication systems during development projects is crucial for long-term security. Authentication on the early internet was a matter of just a single username-password combination, stored in simple text files.
But in a hyper-connected digital age, even the simplest passwords are no longer sufficient — cybersecurity threats are becoming sophisticated, so you need harder, faster forms of authentication.
As networks began to rise, so did authentication mechanisms such as OAuth, OpenID Connect, and SAML. These made it possible to use secure single sign-on (SSO) and cross-platform authentication without having to send the same password over and over.
The past few years have even gone to the extreme of eliminating passwords. Biometric biometric systems such as fingerprint or facial identification and passwordless protocols such as FIDO2 are built to emphasize security while being user-friendly.
Web Authentication Methods
Authentication methods define how the identity or user credential is authenticated against a system. These methods range from simple, old-school approaches to complex, multilayered strategies. Each method relies on specific mechanisms—such as something the user knows (a password), owns (a device), or is (a fingerprint)—to verify their identity and grant access.
1. Password-based Authentication
This is the most traditional approach, whereby users type a special password for their account. Password-based authentication is very simple, but it’s susceptible to phishing and brute-force attacks. Hence, you should seek out more robust passwords and encryption methods.
2. Two-Factor Authentication (2FA)
2FA adds an extra layer of security by requiring a second step of verification. This could be a code sent to a phone or provided by an app, which reduces the likelihood of unauthorized access.
3. Multi-factor Authentication (MFA)
Building on 2FA, MFA employs a combination of multiple criteria in three categories: knowledge (password), possession (token), and inherence (biometric) to offer solid security.
4. Biometric Authentication
This method secures systems using special biological characteristics such as fingerprints or face identification. This makes it highly secure and user-friendly.
5. Token-based Authentication
Tokens, either physical (e.g., hardware keys) or digital (e.g., JWT), serve as secure proof of identity for accessing resources.
6. Certificate-based Authentication
Digital certificates authenticate users via cryptographic keys, providing safe, seamless access to secure systems.
Your choice of authentication method plays a huge role in web application security and ease of use. A poorly configured or complex authentication for a website can frustrate and turn users off from a service, while poor security can lead to data breaches and unauthorized access.
The right approach will depend on the type of platform you run, how sensitive the data is to be secured, and the number of users. A banking app, for instance, might prioritize 2FA or biometrics for tight security, while a content platform may use SSO for easy access. Let’s look deeper into each of these authentication methods.
Password-based Authentication
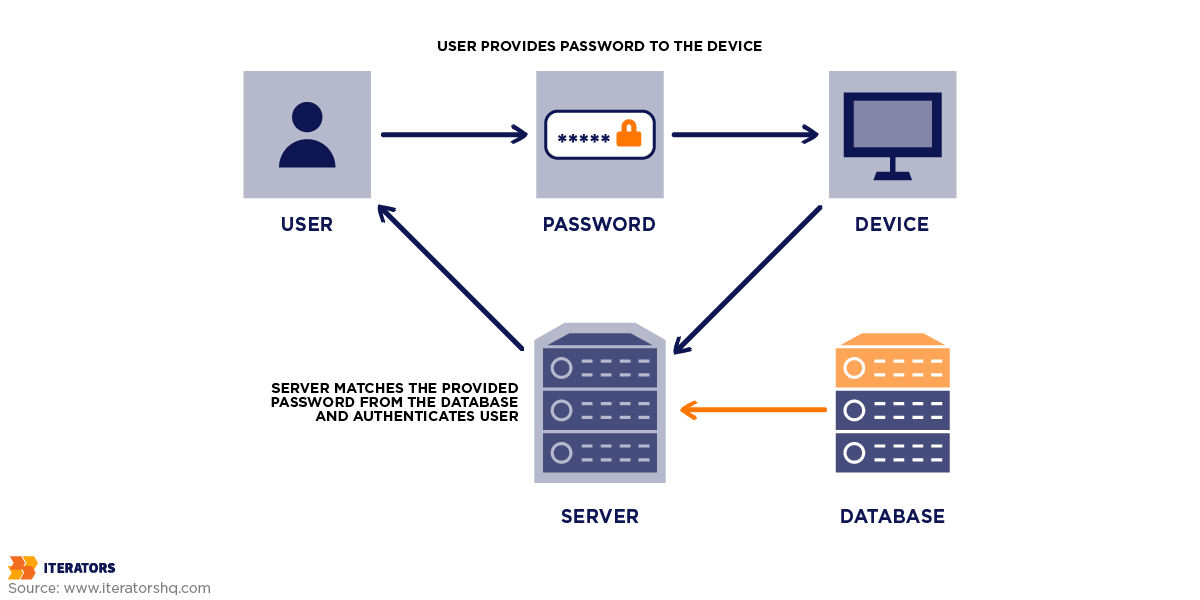
Password is one of the oldest and most popular methods of authenticating a user’s identity. It starts when a user sets up a password in account creation. This password will be stored on the system’s database, usually encrypted or hashed so that no one can get access to it directly.
Each time someone logs in, the system compares the password they type with the record they have. If they are the same, you are accessed, otherwise you are not.
While passwords are easy and familiar for both users and developers, they are usually easy to break and difficult to implement in complex digital landscapes. For this reason, many organizations are moving towards more secure and user-friendly methods such as biometric, token-based and multi-factor authentication (MFA).
Benefits of Password-based Authentication
- Passwords are fairly easy to configure and install into apps.
- People are already used to making and using passwords, so you don’t need to organize extensive training.
- Password systems don’t require much infrastructure compared to more advanced methods.
Challenges and Vulnerabilities
- It’s particularly vulnerable to attacks such as phishing, brute force, and credential stuffing.
- The majority of users make passwords that are simple to guess, or reuse passwords between accounts. In fact, two-thirds of Americans use the same password across multiple accounts.
- Passwords can be forgotten, and this leads to frequent recovery requests.
Best Practices for Password-based Authentication
1. Implement Password Policies
Set strict guidelines for enhancing security like regularly changing the passwords (e.g., every 90 days) and not using old passwords again. These avoid any lingering exposure if a password is compromised.
Also, have rules that force users to use more difficult passwords containing both upper and lowercase letters, numbers, and special characters. Remember, weak passwords are responsible for over 80 percent of data breaches in organizations. Have minimum length requirements (e.g., 12 characters) and do not accept commonly used patterns like “123456” or “qwerty.”.
2. Use Encryption and Hashing
Protect passwords with strong algorithms that are not susceptible to brute force attacks. These could be bcrypt, Argon2, or PBKDF2. Do not store plaintext passwords. Add salting to the hashing so even the same passwords have different hashes, making it even less vulnerable to attackers using pre-calculated hash tables or rainbow tables.
3. Monitor for Suspicious Activity
Monitor and respond to any potential attack such as brute force attacks, credential stuffing, or unusual login behavior. Limit login attempts in case of automated attacks and apply CAPTCHA after many login attempts. Also, notify users if they log in from new devices or locations, and offer to lock accounts when you observe suspicious access. This preventative practice protects users’ accounts and builds trust.
Two-factor Authentication (2FA)
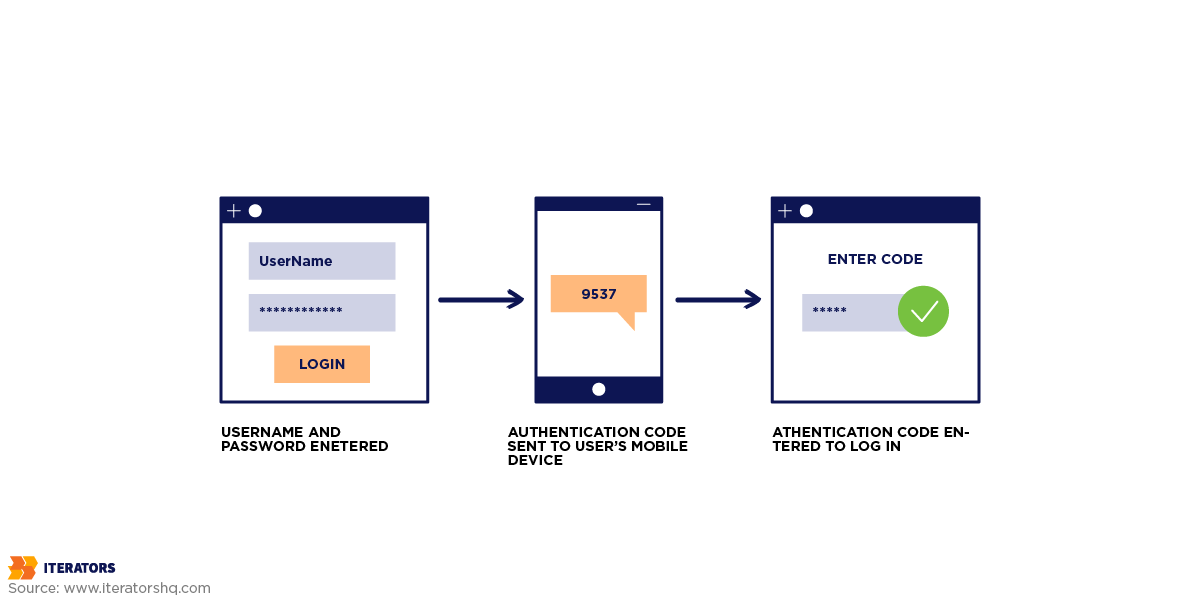
Two-factor authentication (2FA) is a security feature that makes users prove their identity using two authentication methods. Here the user is prompted for the primary account information which is usually a username and password. At the next level, the system asks the user for another verification factor.
The second factor can be a one-time code sent by SMS or email, or a code issued by an authenticator app such as Google Authenticator. Some 2FA may even require a hardware token or key fob. Both factors are verified by the system before it can grant access. Adding a second layer guarantees that even if the primary factor (password) gets hacked, the attacker will still need to have access to the other to open the system.
Two-factor authentication is used in online banking, email, eCommerce, and enterprise tools such as project management software. For instance, when you sign in to a cloud collaboration application like Google Workspace, it normally requires a password and a one-time code. In the same way, payment services such as PayPal use 2FA to secure transactions.
Benefits of Two-Factor Authentication
- 2FA requires two separate inputs, which keeps you safe from unauthorized access even though attackers get around the first step.
- It’s a familiar process for most users due to common tools like SMS, email, or app-generated codes.
- It’s affordable and easy to implement with widespread compatibility across platforms.
Challenges and Vulnerabilities
- Additional steps can cause friction if the second factor is not present (e.g., no phone signal for SMS codes).
- Attackers can use mobile network vulnerability to intercept SMS-based codes.
- If you lose a device (e.g., a phone or hardware token), you may lose the account as well.
Best Practices for Implementing 2FA
1. Choose Secure Second Factors
Consider strong second-factor devices such as app-based authenticators (such as Google Authenticator or Authy) or hardware tokens (such as YubiKey) rather than SMS codes that can be intercepted through SIM swapping or phishing Both app and hardware configurations generate one-time codes locally so they don’t get attacked from the network. Choose secure and user-friendly tools to balance protection with usability.
2. Educate Users
Give users instructions on how to safely set up, store, and operate their second-factors devices. Remind them to always sector secure their app-based authenticators or hardware tokens and the dangers of sharing or losing them. Provide detailed instructions and FAQs to cover the common issues so users are less likely to commit user errors, which could affect account security.
3. Enable Backup Options
Create fallback procedures, such as recovery codes or alternative authentication methods for users to regain access in case their primary second factor fails or is unavailable. Recovery codes must be unique, once-use, and securely stored in the user’s storage. Provide secondary options, such as backups or trusted contacts, so users won’t be permanently locked out in a crisis.
Multi-Factor Authentication (MFA)
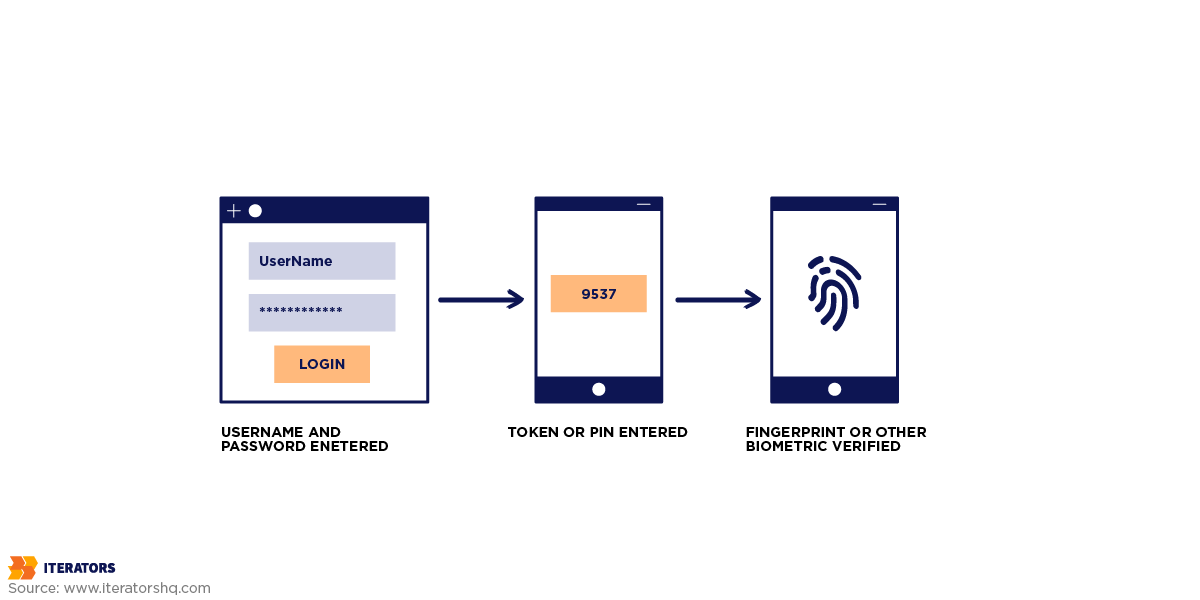
Multi-factor authentication (MFA) is one step more secure than two-factor authentication by requiring more than two verification factors from independent categories. These categories typically include:
- Something You Know: A password or PIN.
- Something You Have: A physical token, smartphone, or smart card.
- Something You Are: Biometric data like a fingerprint, facial recognition, or voice patterns.
Now, imagine you want to make an online purchase using your online banking app. You enter your pin (something you know), then receive a one-time code on your phone (something you have) to verify your identity. If you have biometric authentication enabled, you may also have to scan your fingerprint (something you are) before the transaction goes through. MFA makes sure that it takes more than one layer breach to get to the system since additional factors must be defeated as well.
MFA is most commonly deployed in high-security applications like banking, healthcare, and government. Even cloud services such as Microsoft Azure and Amazon Web Services (AWS) require administrator accounts to use MFA. Even cloud services such as Microsoft Azure and AWS require administrator-level MFA.
Benefits of Multi-Factor Authentication
- MFA is highly protective against unauthorized access even in the case of phishing, credential theft, or brute-force attacks.
- Many industries mandate MFA as part of their compliance requirements, such as HIPAA, PCI DSS, and GDPR.
- Using MFA lets users know their information and accounts are secure.
Challenges and Vulnerabilities
- Implementing MFA in a large organization might take a significant amount of time, money, and training.
- It might be too cumbersome for users if multiple factors are needed for every login.
- While MFA is strong, advanced attacks like man-in-the-middle can still compromise poorly implemented systems.
Best Practices for Multi-Factor Authentication
1. Adopt Adaptive MFA
Use context-sensitive systems that change authentication policies based on where users are, what device they are using, and other behaviors. For example, a recurrent login from a secure device in a normal location might just ask for a password. But if the login attempt is from an unrecognized device, it will require additional verification. This ensures better security and reduces friction for legitimate users.
2. Regularly Audit MFA Systems
Monitor and test MFA systems regularly to find vulnerabilities and make protocols consistent with security guidelines. You may remove old authentication technologies and implement new ones, like FIDO2. Conduct periodic audits and see what user feedback you are receiving on security and usability updates.
3. Provide Alternative MFA Methods
Offer users different MFA options, like app-based authenticators, hardware tokens, biometrics, or SMS codes (as a last resort). This flexibility makes it easily accessible to users with different needs or technical abilities. And it prevents them from bypassing security due to inconvenience or the absence of compatible devices.
Biometric Authentication
Biometric authentication uses physical signatures to prove identity. It’s a much easier and safer alternative to passwords because you’re using something exclusive to you — fingerprints, face, or iris — which makes it difficult to fake or steal.
A user’s biometric (e.g., a fingerprint or a face scan) is extracted and stored in the database of the system. This information is usually encrypted to prevent loss. When a user tries to log in, the system compares the new biometric and the records. If the match is successful, you gain access. Some biometric systems even employ liveness detection to ensure that a biometric input is generated from an actual person, not a photo or replication.
Smartphones and laptops increasingly employ biometric authentication. Apple’s Face ID and Android’s fingerprint recognition are commonly used for unlocking devices and authorizing payments. Likewise, many international airports use face or fingerprint recognition to speed up check-in and boarding.
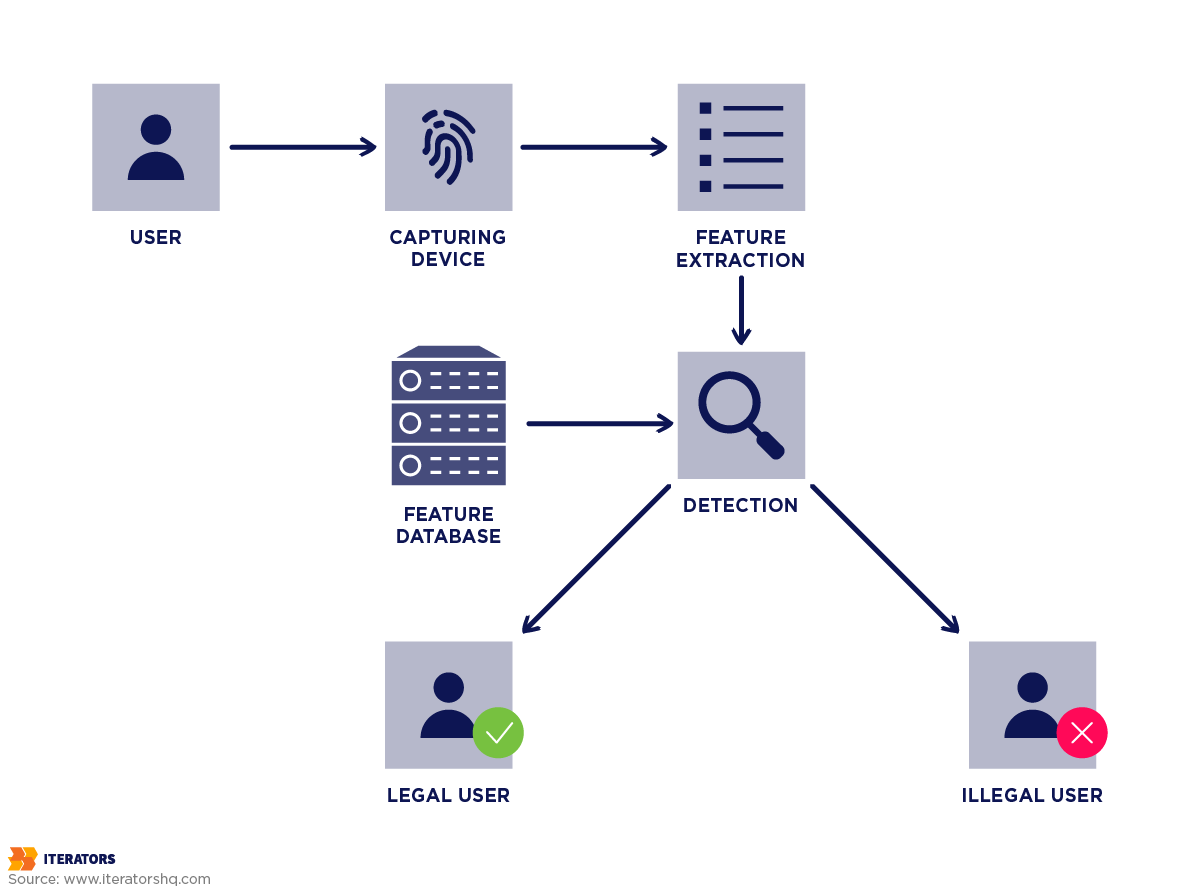
Benefits of Biometric Authentication
- Biometric data is personal and is not easily stolen or copied like passwords and tokens.
- It saves you from having to remember long passwords, offering a frictionless authentication experience.
- Biometrics makes login seamless and quicker than other authentication techniques.
Challenges and Vulnerabilities
- Storing biometric data poses privacy concerns as breaches could expose sensitive personal information.
- In some situations — like wet or scalded fingers for fingerprint recognition or dull lighting for facial recognition — the system might not be able to authenticate correctly.
- The cost of implementing biometrics, especially in a large-scale environment, can be steep and expensive.
Best Practices for Biometric Authentication
1. Use Multimodal Biometrics
Pair various biometrics factors for greater security and reliability. Multi-modal biometrics reduces the chance that the authentication will fail due to environmental conditions (e.g., insufficient lighting or smudged fingerprints) and provides a stronger defense against spoofing attacks.
2. Implement Fail-Safe Options
Offer other types of authentication, such as passwords, PINs, or OTPs to account for scenarios where biometric authentication fails. This prevents users from being locked out due to system failure, physical changes, or other environmental conditions that interfere with biometric recognition.
3. Minimize Biometric Data Retention
Don’t store biometrics beyond the authentication period. Adopt policies to securely destroy old or inactive data to avoid being exposed in the event of a breach. Using secure hash functions to store biometric templates instead of raw data adds an extra layer of protection.
Token-based Authentication
A token-based authentication is an innovative form of authentication where digital tokens are used to verify users and unlock systems, apps, or APIs. Tokens serve as digital keys that can replace passwords to manage authentication for websites more effectively. Here’s how it works:
The user signs in with their credentials, typically a username and password. If approved, the system creates a token for the user. The token is a string of encrypted data — user’s details, session, and expiration time. Instead of re-entering credentials, the token is sent with each request, confirming the user without having to sign in again. The server checks the token before granting access. If the token is invalid or broken, it is rejected, and access is denied.
Here’s a simpler way to picture it: think of a token as a movie ticket. When you buy the ticket, your payment (credentials) is verified, and you’re given the ticket (token). This ticket allows you to enter the theater and move around without showing your payment details repeatedly. However, the ticket is valid only for a specific movie and time (session expiration). If you try to reuse it or modify it (broken or invalid token), access will be denied.
Token-based authentication is one of the most fundamental elements of API security since it can be used to sign up users or apps without sending the same credentials repeatedly. Popular platforms like Google and Facebook also use tokens for session management, enabling seamless interactions across their services.
Benefits of Token-based Authentication
- Tokens are usually limited and time sensitive so they are less susceptible to fraud than passwords.
- Tokens provide stateless authentication — meaning the server does not store session data, which provides better scalability and performance.
- If a token is compromised, it can be revoked without affecting other users or the system.
Challenges and Vulnerabilities
- If hackers intercept a token, they have unauthorized access until the token runs out or is revoked.
- There’s a tradeoff between token expiration time — the shorter the period, the more users get irritated, and the longer the time, the higher the security risks.
- If you do not store tokens properly on the client, it might be vulnerable to cross-site scripting (XSS).
Best Practices for Token-based Authentication
1. Use Secure Protocols
Send tokens only on encrypted channels such as HTTPS so they can not be read by hackers. Secure communication keeps sensitive token information secure during transmission so there is virtually no possibility of man-in-the-middle attacks or unauthorized access.
2. Implement Short-Lived Tokens with Refresh Mechanisms
Use tokens with short expirations so they’re not very usable if someone steals them. At the same time, set refresh tokens for longer sessions so that they are constantly refreshed with new access tokens without needing to re-login. This approach gives security and user comfort by minimizing token lifespans while keeping sessions alive.
3. Use Token Scopes and Permissions
Limit the power of tokens by defining scopes or permissions to restrict access. For instance, a read token can’t have write access. This least privilege rule minimizes the risk of token abuse or compromise.
Certificate-based Authentication

Certificate authentication is based on the use of digital certificates to authenticate a user or device. These certificates are issued by a reliable Certificate Authority (CA). They include cryptographic keys, the issuer’s name, and an expiration date.
When a user or device sends the certificate to the server, the server confirms the validity of the certificate by comparing the signed certificate with the public key of the CA. If valid, the server uses the public key to establish a secure communication channel.
For example, a remote worker accessing confidential files on the company’s intranet uses a digital certificate to verify their device and establish a secure connection. Similarly, in IoT ecosystems, certificates authenticate smart devices like home assistants or industrial sensors, ensuring they can securely exchange data without being tampered with. In web security, SSL/TLS certificates encrypt communication between the browsers and the server.
Benefits of Certificate-based Authentication
- Certificates are built on public key infrastructure (PKI) that is very hard to hack.
- It does not need passwords so there are no risks of phishing or brute-force attacks.
- Certificates can authenticate thousands of users or devices with no system updates required.
Challenges and Vulnerabilities
- Keeping track of the certificate expiration and revocation can be tedious, especially for large enterprises.
- Licensed certificates from reputable CAs often involve licensing fees, which adds to the implementation costs.
- If certificates’ private keys are stolen, they can be used for unauthorized access.
Best Practices for Certificate-based Authentication
1. Automate Certificate Management
Use automation tools to handle the certificate lifecycle, including renewal, revocation, and deployment. Popular automation tools like AWS Certificate Manager and DigiCert CertCentral can help you manage deployments on a massive scale, and reduce human error. Automated certificates do not lead to problems or breaches when they expire.
2. Protect Private Keys
Store private keys in a safe place, such as Hardware Security Modules (HSMs), where you won’t let anyone access them. You also need to protect private keys with strong encryption while storing and sending. Private keys must be secure to keep the trust intact, as it will be easy for hackers to impersonate or decrypt.
3. Implement Certificate Pinning
Apply certificate pinning to limit systems to trusted, known certificates. This minimizes the chance of man-in-the-middle attacks. By checking certificates against a list of trusted sources, organizations can block bad certificates from compromised or rogue CAs.
Common Authentication Protocols
An authentication protocol is a set of policies or frameworks for verifying identities in digital environments. These protocols provide encrypted messaging, data security, and simplified access control. Here are some of the most popular authentication protocols:
1. OAuth
Open authorization or OAuth is an open token security standard. It lets users grant third-party apps limited access to resources without disclosing their login details. Rather than logging in, users register with an identity provider (e.g., Google) and send the app a token that is used for temporary access.
OAuth is the most common method of SSO (single sign-on) or authorization for social media sites or cloud services. However, it is not authentication-oriented. This means that it does not check user credentials but allows secure delegation of access.
2. OAuth 2.0
OAuth 2.0 is a better, scalable, and more secure version of OAuth. It uses access tokens to let third-party applications access user resources without revealing credentials. OAuth 2.0 is more granular and it provides various authorization flows for web, mobile, and APIs.
It is commonly integrated with Facebook, Google, or Microsoft products and provides sandboxed SSO and integration with third-party tools. However, OAuth 2.0 is more about authorization than authentication. Developers often use it alongside protocols such as OpenID Connect (OIDC) to validate identity.
3. OpenID Connect (OIDC)
OpenID Connect (OIDC) is an identity layer based on OAuth 2.0, specifically for authentication. It enables users to authenticate with an identity provider they trust (e.g., Google), and communicate that authenticated information to external applications. OIDC also makes authentication easy using JSON Web Tokens (JWT) for anonymously exchanging user identity information.
It is widely used for single sign-on (SSO) in websites and mobile apps to provide a user-friendly experience. Combining authentication with OAuth 2.0 authorization allows OIDC to provide fast and secure identity verification and resource access.
4. SAML (Security Assertion Markup Language)
SAML is an XML-based protocol used to exchange authentication and authorization information between an identity provider and a service provider. It is often used in companies to provide SSO for users from multiple authenticated applications or systems.
SAML allows for easy administration of users as authentication is centralized, meaning that you don’t have to worry about a lot of passwords. It works by sending security claims, including user credentials and roles over encrypted channels. SAML is especially common in business and government environments where security and interoperability between platforms are important.
5. FIDO2
FIDO2 is an authentication standard that was created by the FIDO Alliance to eliminate passwords. It uses public key cryptography to authenticate users through hardware security keys, biometrics, or PINs. FIDO2 contains two parts: WebAuthn (an HTTP API provided in the browser) and CTAP (Client to Authenticator Protocol).
This standard makes passwordless authentication secure, fast, and easy to use. It guards against phishing and credential theft since credentials never leave the device. FIDO2 is adopted by all browsers and operating systems to ensure that we can finally move towards a password-less future for secure web authentication.
6. Kerberos
Kerberos is a network authentication protocol used for distributed access. It operates through a ticket mechanism with a third party, the Key Distribution Center (KDC), issuing tickets to verify user accounts. These tickets permit customers to log in to services without entering credentials over and over again.
Kerberos uses symmetric encryption to protect communication from eavesdropping or replay. It is widely used in enterprise environments to sign in users to Windows domains or any system that requires sophisticated, centralized security.
7. LDAP (Lightweight Directory Access Protocol)
LDAP is a protocol to access and operate directory services over a network. It allows central authentication by storing the credentials and permissions of the user in a directory server. Applications or systems query the LDAP server to authenticate users and confirm their permissions.
LDAP supports hierarchical data storage, making it efficient for large organizations with complex user structures. It integrates with Active Directory and other directory services to provide a single authentication infrastructure, resulting in secure and efficient user management.
| Protocol | Best For | Key Features | When to Use |
| OAuth | Authorization for third-party apps | Token-based, open standard | Use for delegating access without sharing credentials, e.g. connecting apps with social media. |
| OAuth 2.0 | Advanced authorization for modern apps | Scalable, support APIs, granular flow | Choose for robust secure API and app integration needing advanced integration |
| OIDC | Authentication with identity verification | JSON Web Tokens, built on OAuth 2.0 | It is ideal for SSO and user authentication in web and mobile apps |
| SAML | Enterprise SSO and interoperability | XML-based centralized authentication | Best for enterprise environments needing secure access across legacy and cloud systems |
| FIDO2 | Passwordless authentication | Public key cryptography, biometrics | Best for strong phishing-resistance authentication in modern web environments |
| Kerberos | Secure network authentication in enterprise environments | Ticket-based, uses symmetric encryption | Suitable for managing distributed access in corporate or Windows domain networks. |
| LDAP | Centralized authentication with directory services | Hierarchical data storage, efficient querying | Ideal for large organizations needing centralized user and permission management. |
Common Pitfalls in Implementing Authentication

Authentication is key to security, but a lot of implementations make basic security mistakes. Here are some of the most common pitfalls and their consequences.
1. Weak Password Policies
Weak password policies open systems to brute-force and dictionary attacks. Some errors the development team makes include accepting short passwords, not asking for complexity (for example, a combination of letters, numbers, and symbols), and not requiring change regularly. Password reuse is another issue they often fail to address.
Policies must require minimum password lengths (12 characters minimum), and complexity, and prohibit reusing passwords. Adding multi-factor authentication (MFA) to your passwords gives an extra layer of security and makes it less vulnerable to unauthorized access.
2. Poor Session Management
Errors in session management can cause unauthorized access if sessions aren’t well secured. For instance, having predictable or weak session IDs can be easy for attackers to guess. Leaving sessions running for days without an end makes them more vulnerable to cookie or token theft.
For proper session management, create secure, random session identifiers, allow expiration timeouts when you are not using the session, and implement secure logout options. You could also encrypt session data and mark cookies as “HTTPOnly” and “Secure,”. This adds more security against unauthorized access or interceptions during transmission.
3. Insecure Storage and Transmission
It’s also a major mistake to store credentials, tokens, or other data as plaintext, as it provides attackers direct access in case of system intrusion. Also, when authentication data is sent through open interfaces like HTTP, it can be hacked using man-in-the-middle attacks.
Robust encryption plays a vital role in achieving data integrity. Most ideally, you would protect data in the background with an encryption algorithm such as AES-256 and protect data in transit with TLS (Transport Layer Security). Also, you can have hash-and-salt algorithms for passwords and change encryption keys periodically to keep people from gaining unauthorized access.
4. Configuration Errors
Misconfigurations and business logic flaws often cause system vulnerabilities. For example, leaving default credentials enabled, misconfiguring token expiration, or forgetting to lock down API access. Pre-installed configurations often leave systems susceptible to exploits.
It’s therefore critical to update and audit the configurations on a regular basis for security reasons. Use automated tools to spot inefficiencies and adopt secure defaults to keep systems secure even when manual settings are missing or forgotten.
5. Overlooking Social Engineering Attacks
Authentication can fail if attackers cheat the system through social engineering. Pseudo-hacking attacks, for example, trick you into sharing passwords or MFA codes. These strategies are usually successful because people don’t know about them.
A good way to patch up this weakness is to train users to spot phishing attempts. You can also implement technical measures such as email filters and domain tracking. Anti-phishing MFA mechanisms such as security keys or biometrics are also very effective in reducing reliance on human vigilance alone.
Key Considerations When Selecting a Web Authentication Solution
When choosing a web authentication platform, you need to think about the following factors:
1. Security Level

The first and foremost thing is that the solution should be secure. It has to guard against brute-force attacks, credential stuffing, and phishing. Solutions must include multi-factor authentication (MFA), password hashing, and encryption for data at rest and in transit.
Solutions that support advanced security methods like biometrics or physical security keys also provide an extra layer of protection. Regular security patches and compliances, such as GDPR, PCI DSS, or FIDO2 are also essential to keep your systems resilient against changing threats.
2. User Experience
A frictionless user experience is the key to wide adoption. If your users authentication methods are too tight or complex, users may get frustrated and abandon the workflow. Solutions need to be both secure and easy to use. Consider using single sign-on (SSO) or biometric authentication for speedy access.
Passwordless authentication, such as magic links or QR codes, can be frictionless but secure. You can also customize branding the login page to instill user trust and make the experience even more user-friendly.
3. Scalability
As companies grow, their authentication systems must be capable of handling more users and usage. The ideal solution should accommodate high traffic without compromising performance. It should evolve with additional features as necessary.
Cloud authentication solutions like Azure AD or Okta, for example, often offer scalability and security. Consider solutions with federated identity functionality, which allows organizations to have user accounts across multiple platforms or partners.
4. Compatibility
System integrations are a key consideration when choosing a web authentication provider. An authentication solution should work with your current infrastructure, apps, and protocols. Compatibility with standards such as OAuth 2.0, OpenID Connect (OIDC), or SAML means you can integrate with different platforms.
The right authentication method should also be supported by different devices and OS, including desktops, mobile devices, and IoT devices. Consider using API-based solutions for their flexibility. Developers can easily embed them in custom apps or workflows.
Future Trends in Web Authentication
As cyber threats evolve, so do the methods for securing online identities. These are some of the new trends that are defining the future of web authentication:
1. Passwordless Authentication
Passwordless authentication is gaining popularity as it promises to eliminate the risks associated with traditional passwords. It involves the use of biometrics (fingerprints, face recognition), security keys, and magic links to authenticate users. This removes the password from the game, preventing attacks like brute-force attacks and credential theft.
Passwordless solutions are also user-friendly because they make logging in much simpler, especially on mobile devices and IoT systems. The global passwordless authentication market is expected to grow from $18.82 billion in 2024 to $60.34 billion by 2032.
2. AI and Machine Learning in Authentication

Artificial Intelligence (AI) and Machine Learning (ML) are transforming authentication through the adoption of adaptive and behavioral security. These solutions monitor data from user behavior — how fast you type, how you use the device, where you log in from — to look for anomalies that might reveal fraud or unauthorized use.
BioCatch is one of the top companies making waves in this field. They specialize in behavioral biometrics, analyzing patterns such as mouse movements, typing cadence, and touchscreen interactions to identify legitimate users. Today, 34 of the world’s top 100 banks and 237 total financial organizations employ BioCatch Connect™ to mitigate fraud.
3. Decentralized Identity
Decentralized identity moves digital identity management from central servers to users themselves. Based on blockchain technology, it allows you to generate, store, and transfer identity credentials without having to trust a single provider.
Decentralized identity solutions such as Microsoft’s Azure Decentralized Identity or the Sovrin Network promise more privacy since your data is held locally or distributed ledgers instead of on a central server. This way it avoids large-scale data breaches, which is in line with privacy regulations such as GDPR. The decentralised identity market is expected to grow at a compound annual growth rate (CAGR) of 90.3 percent from 2023 to 2030.
4. Quantum Communication and Cybersecurity
Quantum computing presents authentication problems as well as solutions. While quantum computers may compromise encryption protocols, quantum communications techniques like Quantum Key Distribution (QKD) are far more secure.
QKD employs quantum mechanics principles to encode keys which are nearly impenetrable to the entrapment process. Although still in development, quantum-secure authentication techniques will become more important to secure sensitive systems as quantum computing evolves. The global quantum communication market is expected to grow from $0.74bn in 2024 to an estimated $5.54bn by 2030.
5. Zero Trust Architecture
Zero Trust Architecture (ZTA) is an authentication revolution that presupposes that no user, device, or application can be trusted. Rather, it checks user identity and device posture continuously at each access point, regardless of where they’re sitting or when they first logged in.
ZTA is guided by concepts such as least privilege access and micro-segmentation where users have only access to what they require. With robust authentication and continuous monitoring, ZTA improves security and resilience in complex IT environments. Experts predict that by 2032, the global zero trust market is expected to reach $133 billion, up from around $32 billion in 2023.
Elevate Your Security Strategy
While passwords are easy and familiar for both users and developers, they are usually easy to break and difficult to implement in complex digital landscapes. For this reason, many organizations are moving towards more secure and user-friendly methods such as biometric, token-based and multi-factor authentication (MFA).
If you’re ready to implement web authentication methods in your products or systems, you’ll have to work with a reliable tech partner. Fortunately, Iterators has built a reputation as a leading provider of robust, secure, and easy-to-use web authentication products.
With the use of cutting-edge technologies and the latest protocols, we provide businesses with secure web development solutions. Our products are both high-security and easy-to-use. They plug into your current infrastructure with minimal disruption.
Take the next step in reinforcing your security strategy. Partner with Iterators to safeguard your business and build a foundation of trust and security. Contact us today to learn more.
